Hi again! I’m continuing with a series of Microsoft Teams Rooms on Windows posts. I’ve not written a ton around the “Windows” side of the Microsoft Device ecosystem. I’ve focused mostly on the “Android” side with Teams Phone & Teams Displays. I’ve also written a number of articles on SIP Gateway and other interoperability solutions. I want to put additional focus on the Windows side, so, consider this the “third” in a never ending (haha!) series of topics around Teams Room on Windows. Here are the first two:
For today, I’m going to focus on Teams Rooms on Windows Intune Enrollment, Intune Compliance & Conditional Access. To start, as I typically do, I want to draw your attention towards our Teams Devices Deployment Playbook found alongside many other amazing IT Pro resources on the Teams Academy. At the time of this writing, slides 24 & 25 have our “top down approach” to successfully deploying Microsoft Teams Rooms on Windows devices.
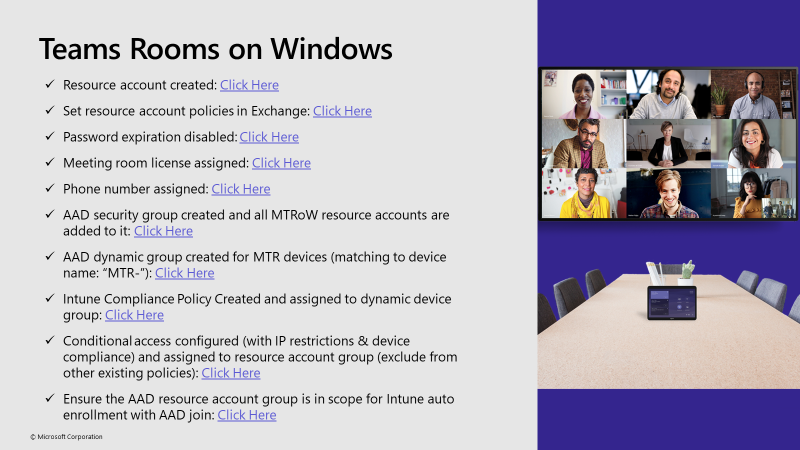
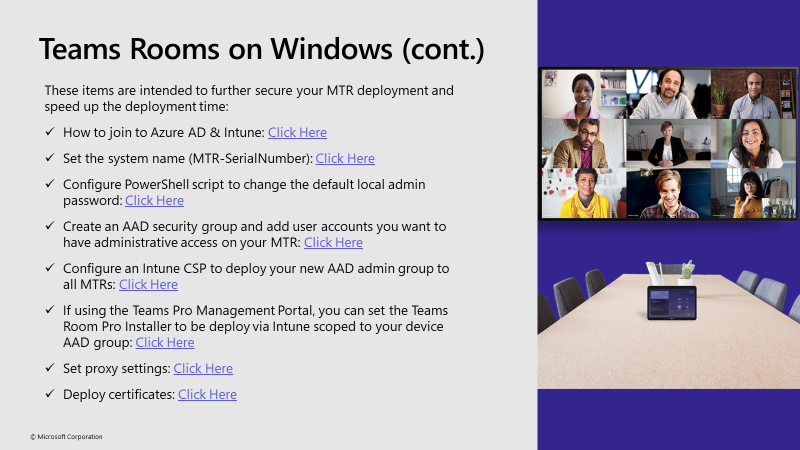
Prep Work
We’ll pick up today assuming you’ve done much of the initial account creation & setup, exchange policy adjustment, license assignment, etc. Specifically, for today’s blog post, I am looking to deploy a Lenovo ThinkSmart Core device out of the box. My account I plan to use is lenovo-core@mydemo365.com and it’s all setup properly. We’ll start today with Azure AD groups. I’ll point out the Playbook items along the way.

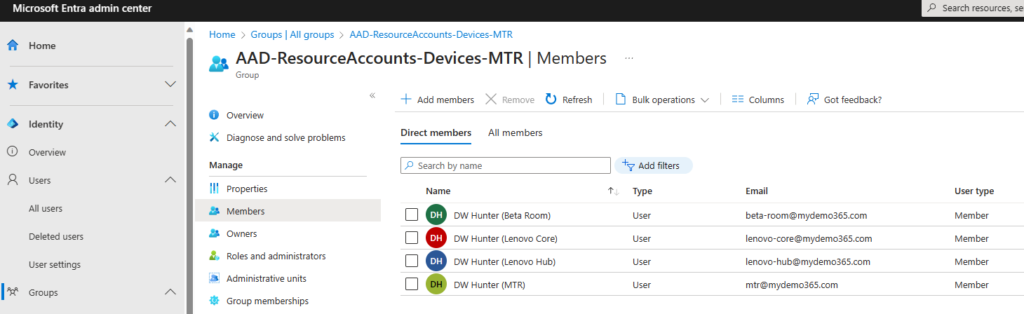
Check! All set!

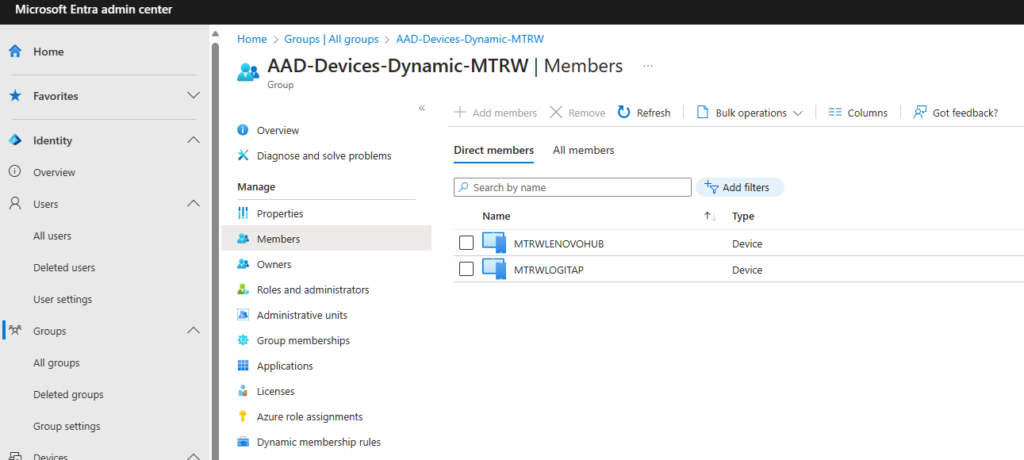
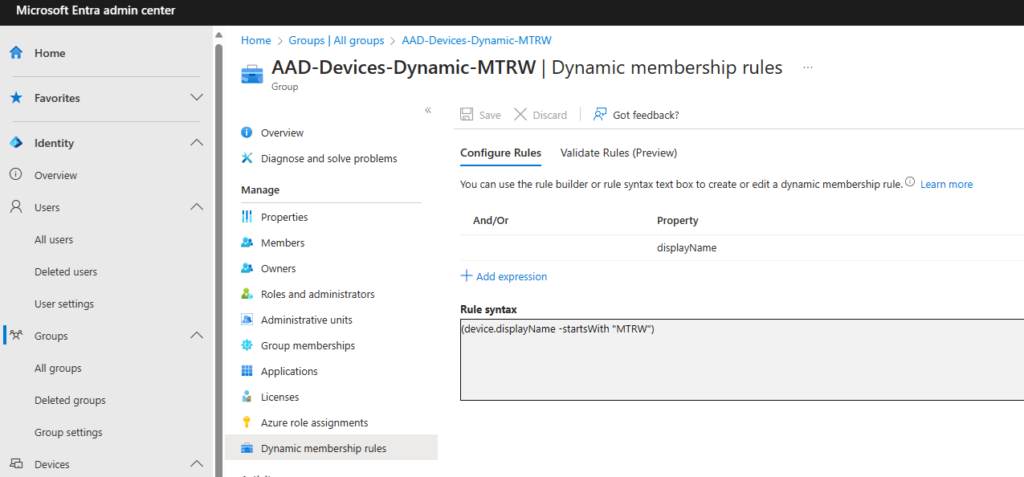
Check! I don’t use MTR- as my naming standard. Instead, I use MTRW and you can see my group above that contains my existing Lenovo ThinkSmart Hub and Logi TAP devices. My dynamic membership rule is below.
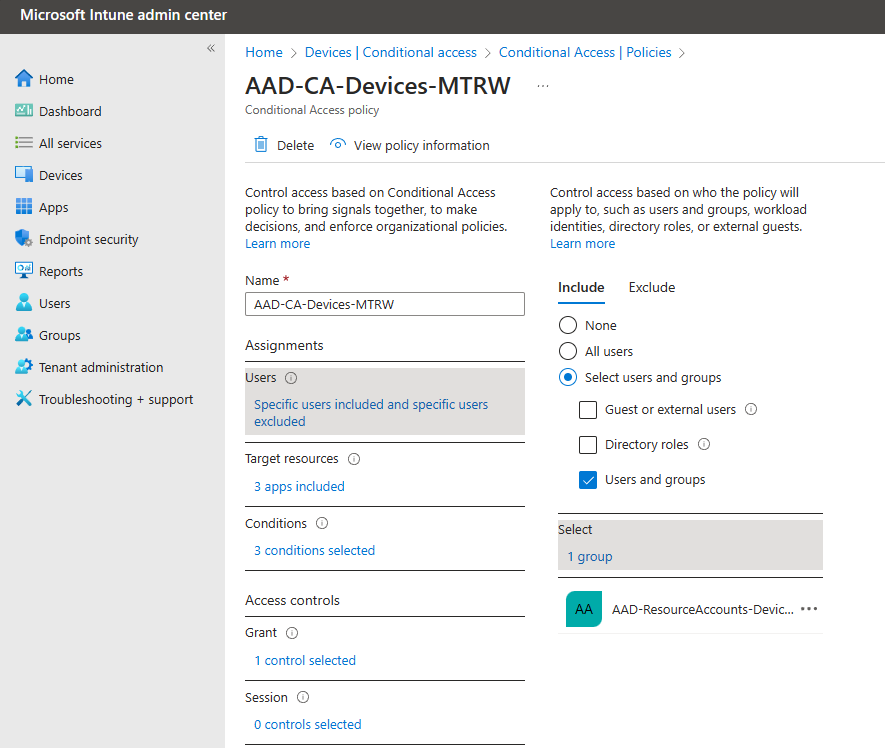
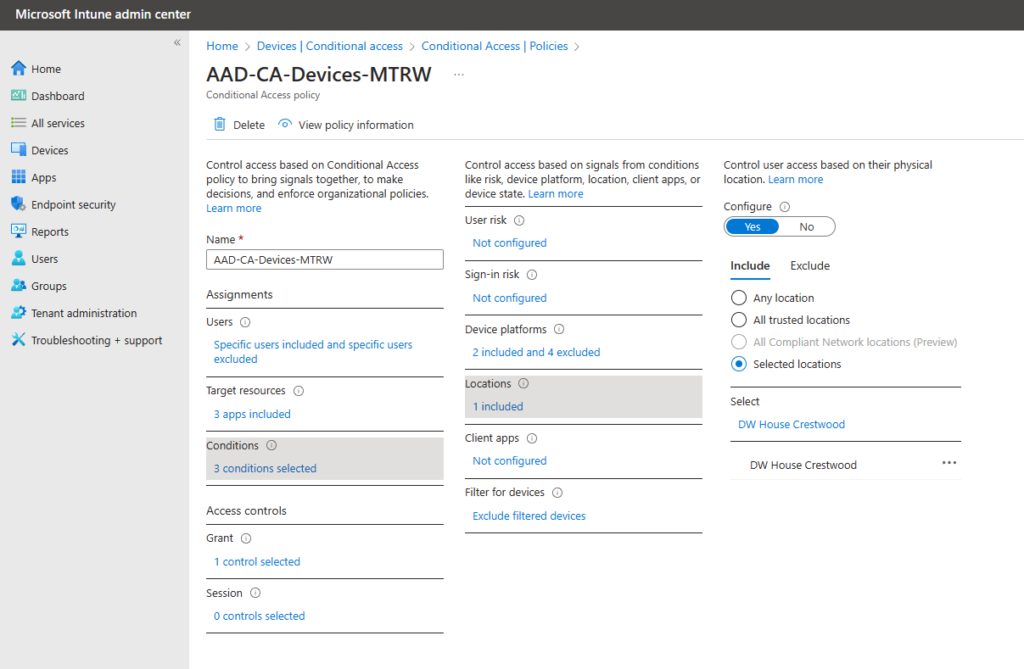
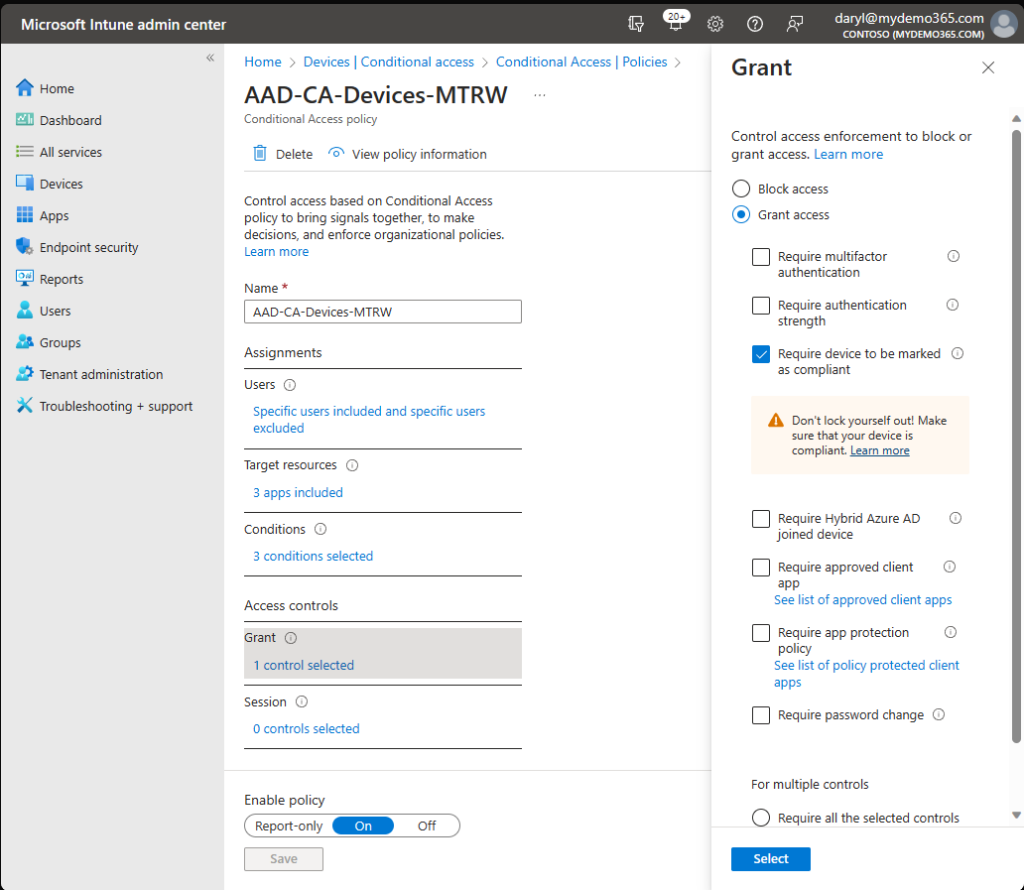
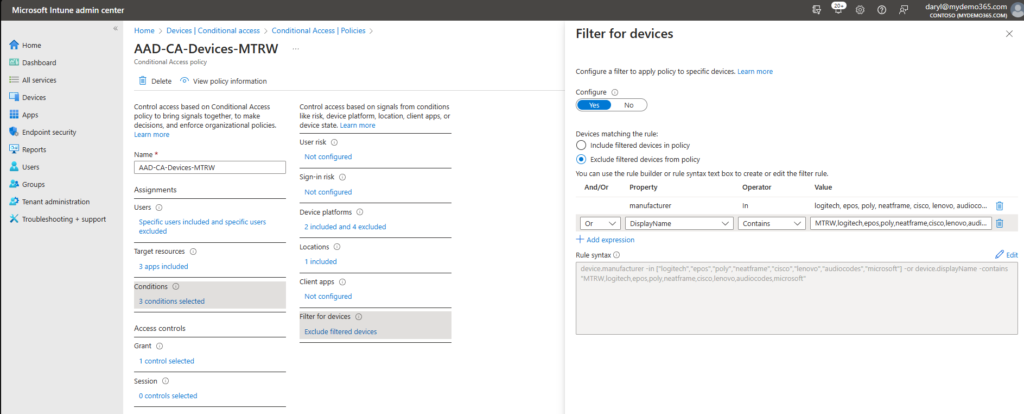
Check! Here are a few screen captures showing my CA Policy assigned to the Resource Account group referenced above. You can also see my IP restrictions (confined to my house in Crestwood, Kentucky), compliance required, and also the device filter exclusions I use to avoid the “chicken and the egg” scenario when it comes to user-based CA and device-based compliance. You can read more from my colleague Traci Herr’s amazing post I’ll drop them below without annotation.

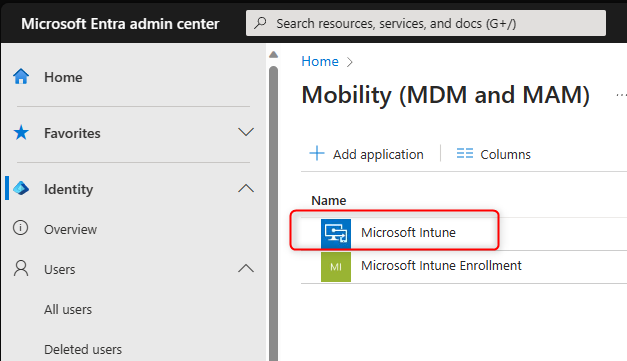
Check! This is handled via Azure AD (Entra ID) MDM & MAM. You can “search” for it in the Azure AD (Entra ID) search screen and then choose the Microsoft Intune option.

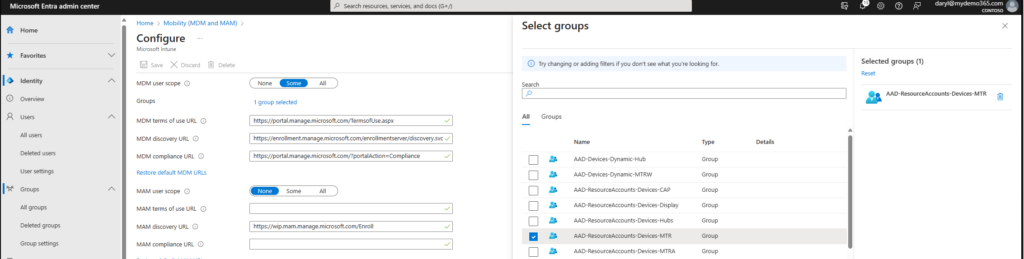
And once again we’ll target the Resource Account group that we’ve been discussing so far in this blog
Bring It All Together
So now what? We have a lot of “prep work” done in the various M365 Admin console. But, we haven’t touched the device yet. So what are some of those items that are required here? Well, if you recall, we setup a dynamic group targeting devices with a certain naming standard. So, we should make sure the device meets that standard. For this example, I’ll manually change the device name. Currently it’s set to the OOBE randomly generated name. So, I want to navigate to Settings -> System and rename the device.
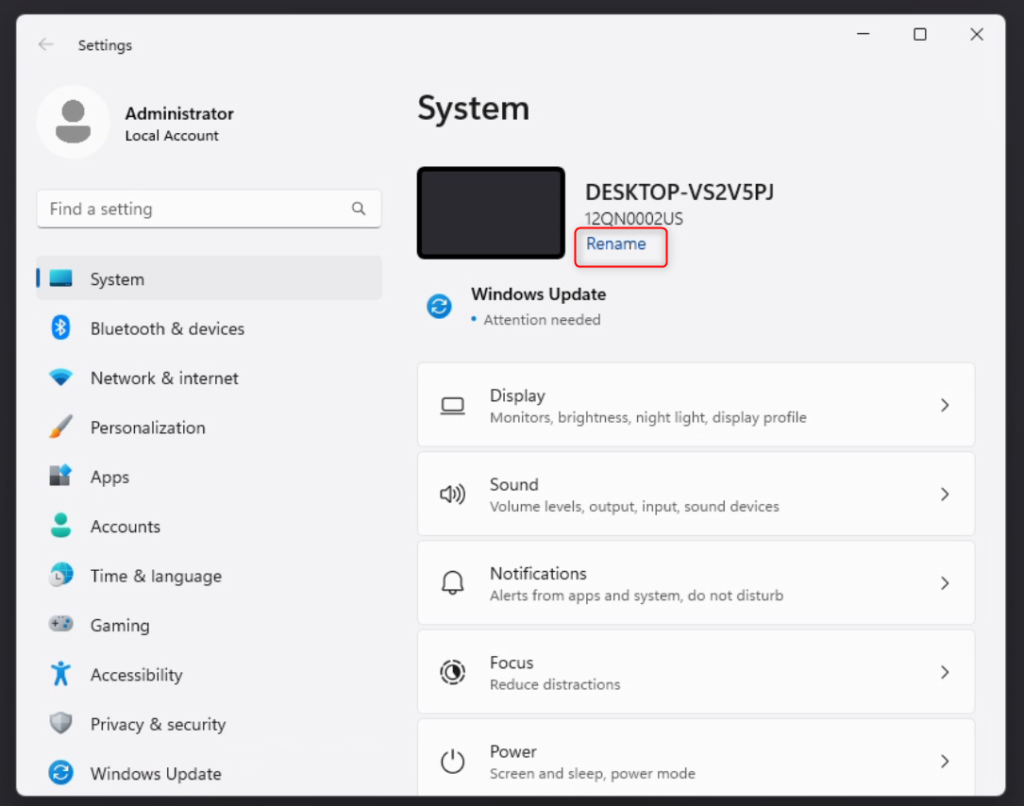
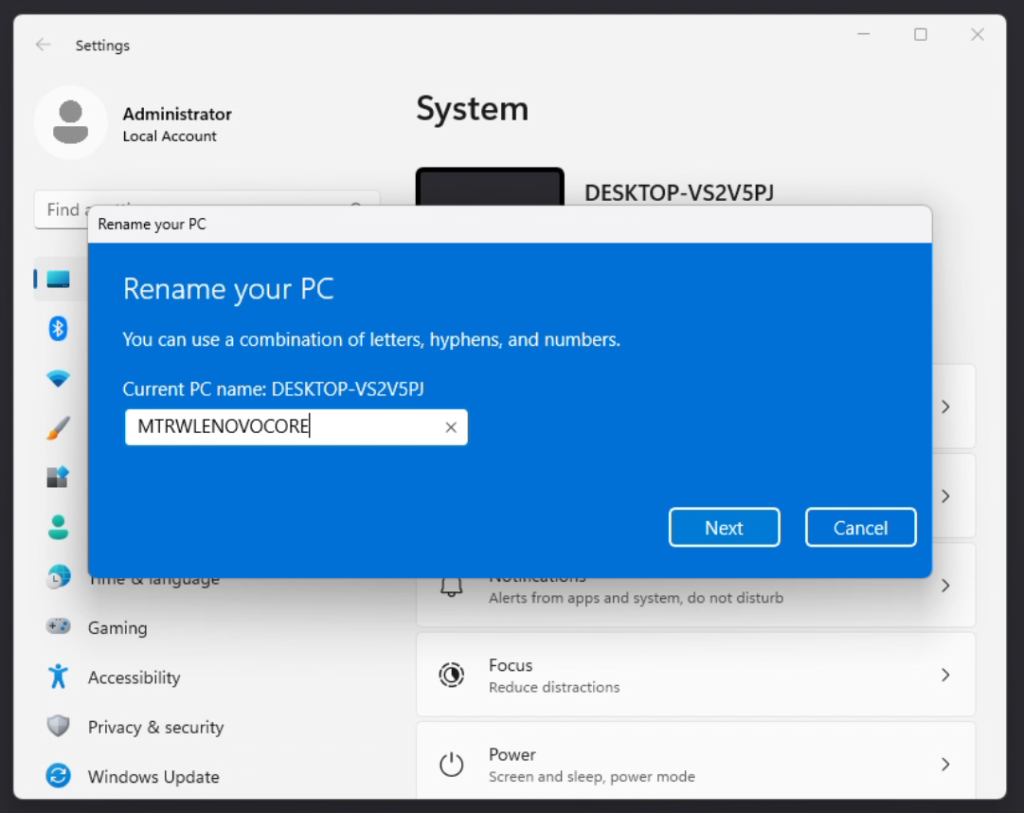
And now when I reboot the computer, it’ll reference the name that meets my naming standard so when I join this device to Azure AD (Entra ID) it will properly be targeted for enrollment and Intune compliance.
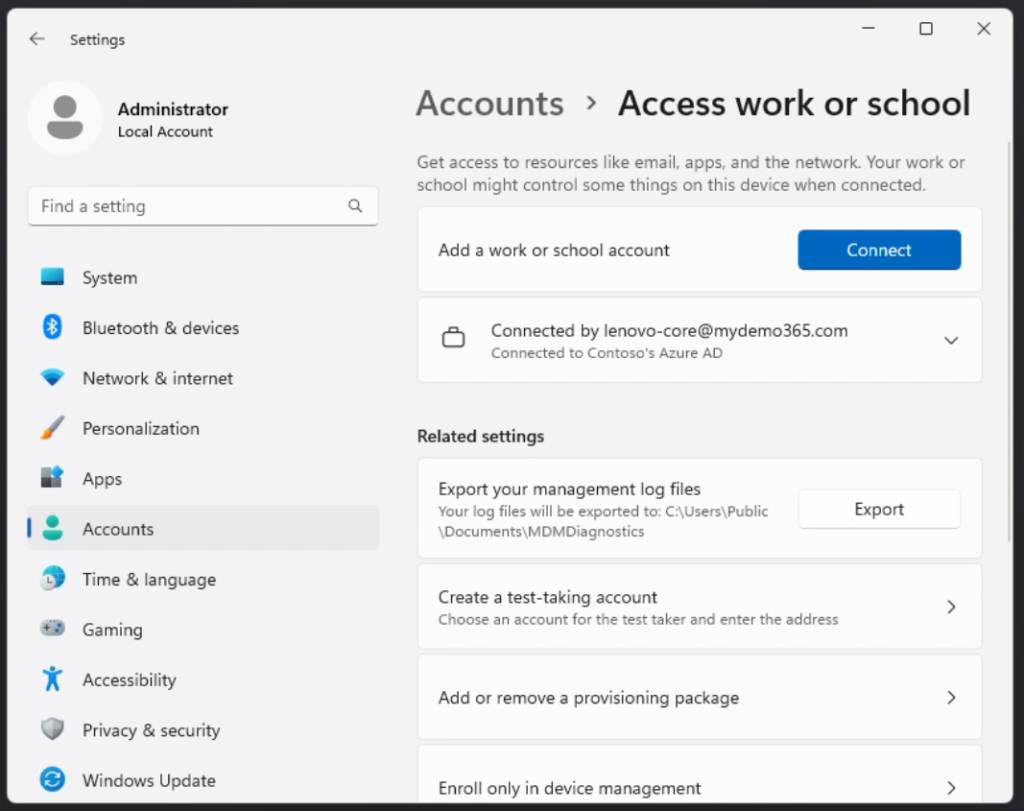
So let’s do that. We’ll want to head over to Settings -> Accounts -> Access work or school
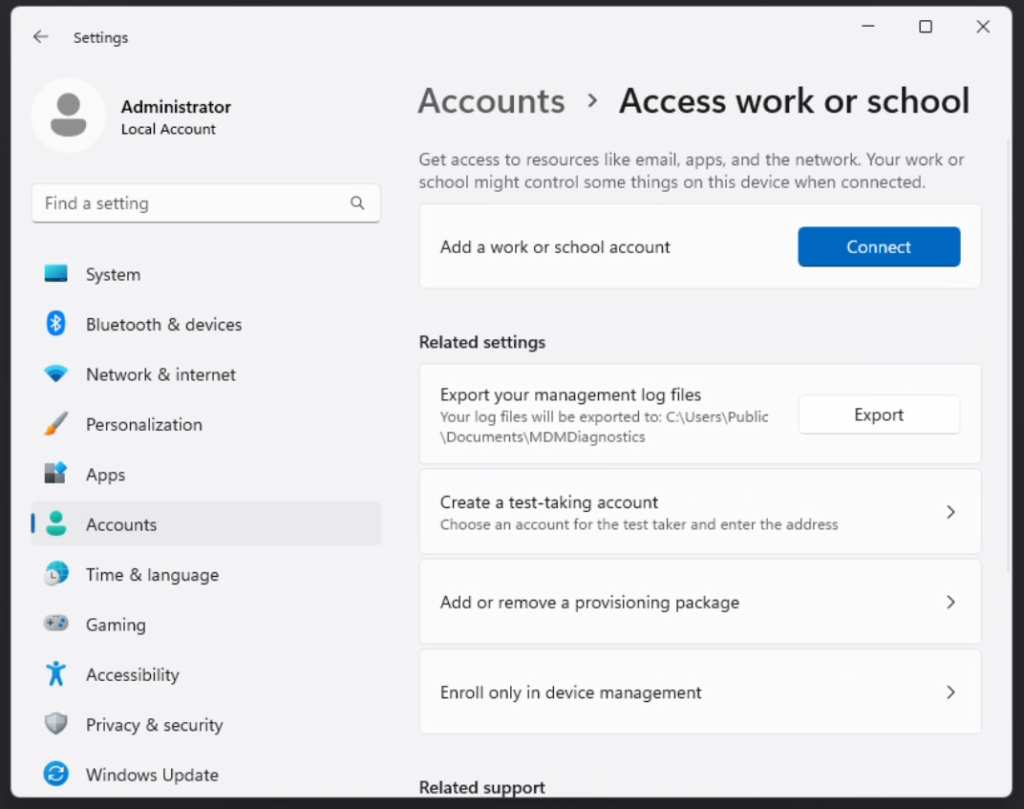
Click the blue Connect button and then you’ll want to “Join this device to Azure Active Directory”
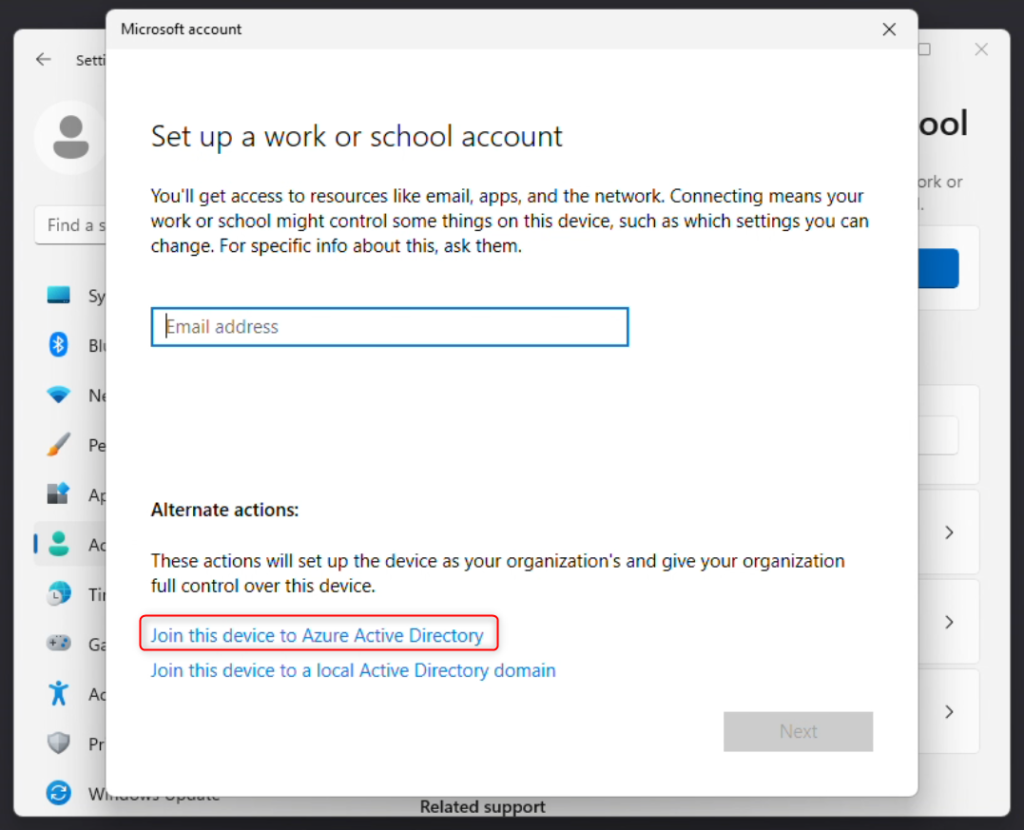
I’ll add a few unannotated screen captures of the process below for you to see.
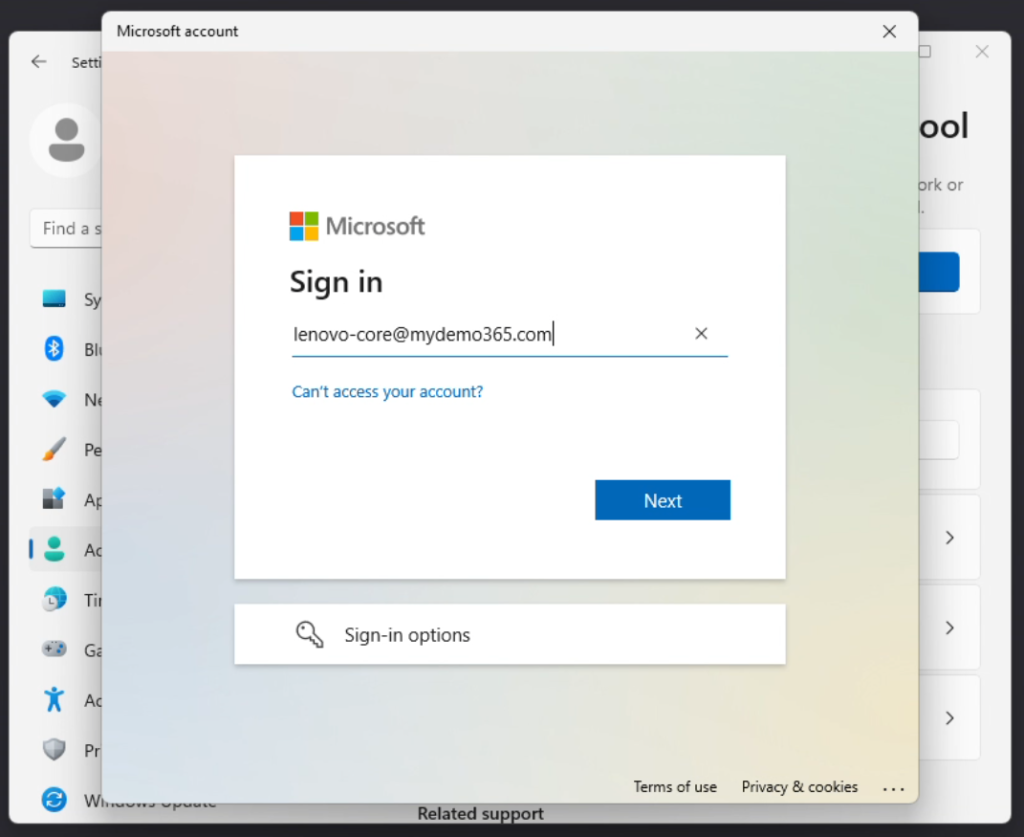
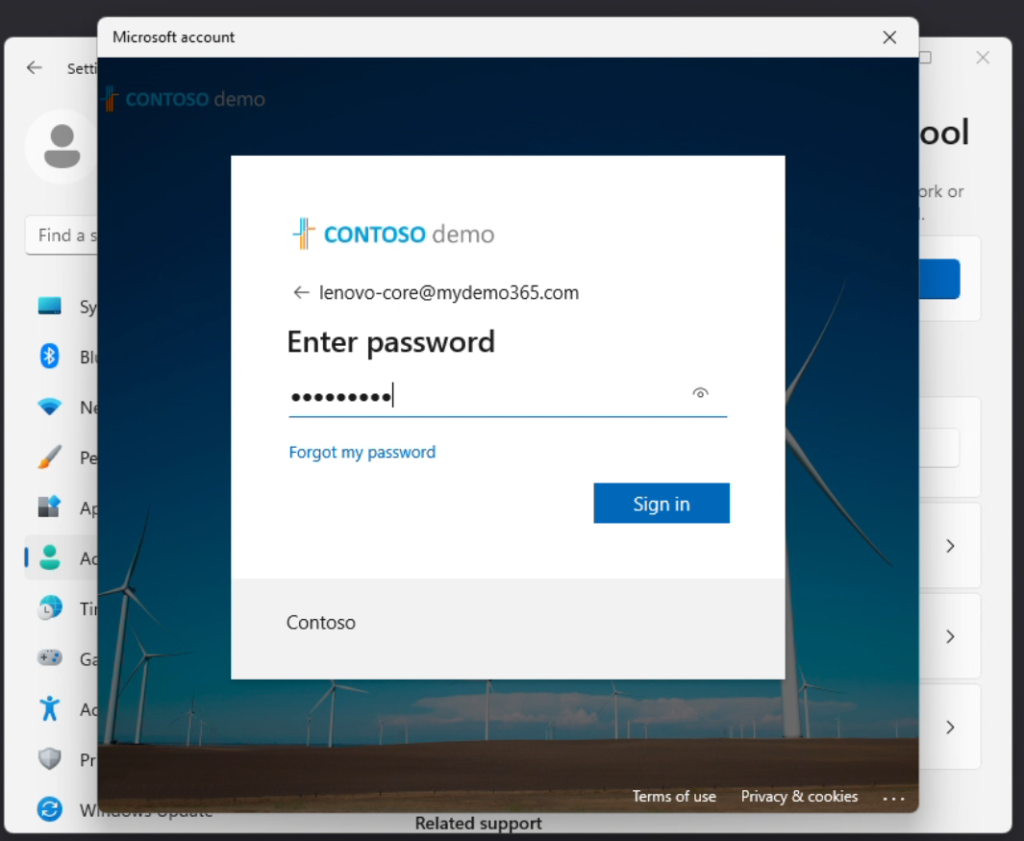
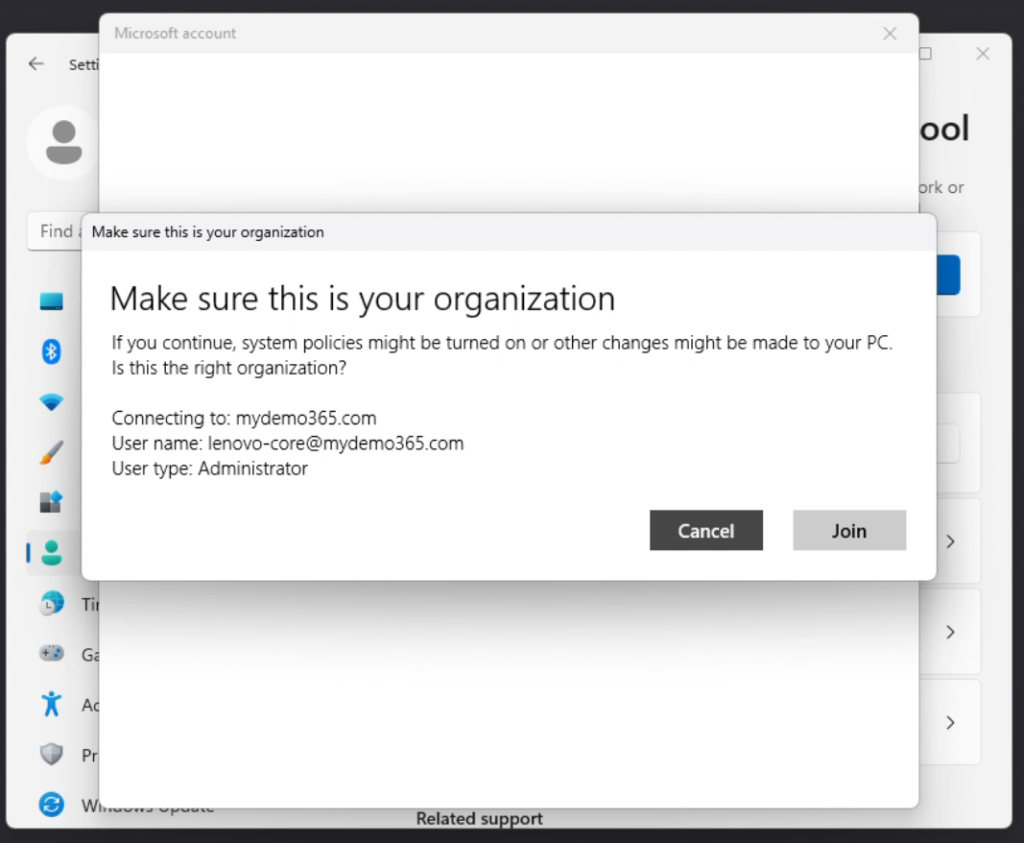
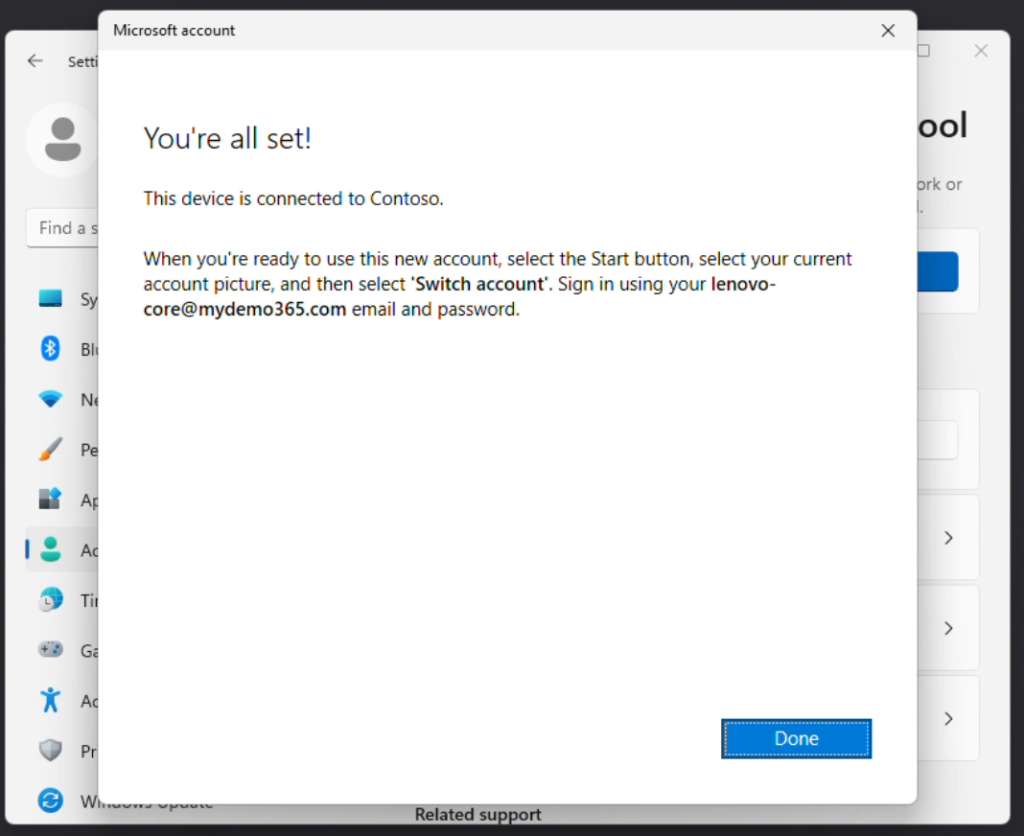
Okay. I’m now joined. And now is a good time to potentially review one of my earlier blog posts at the top of the page to learn more about delegating device administration to an Azure AD (Entra ID) group.
Let’s head to the Azure AD (Entra ID) Devices section and see if the join worked correctly.
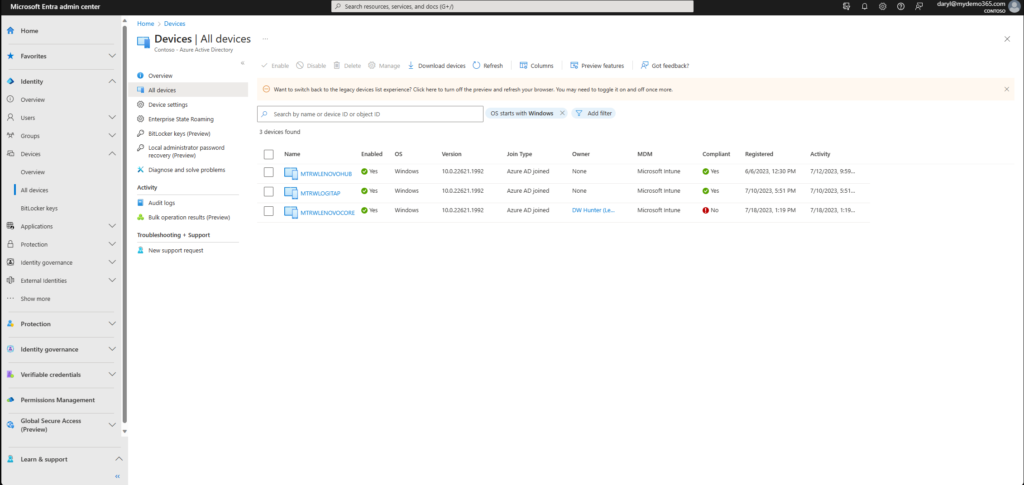
Yup! It did. But, I have some work yet to do. It’s not compliant yet. That’s expected right now as compliance is targeted toward the Dynamic group – so – it will take a little time to get all of that kicked off. But, I do see I need to remove “Lenovo Core” as the owner of this device. It’s a shared device, so, I have some cleanup work to do. All of this is addressed in the Playbook.
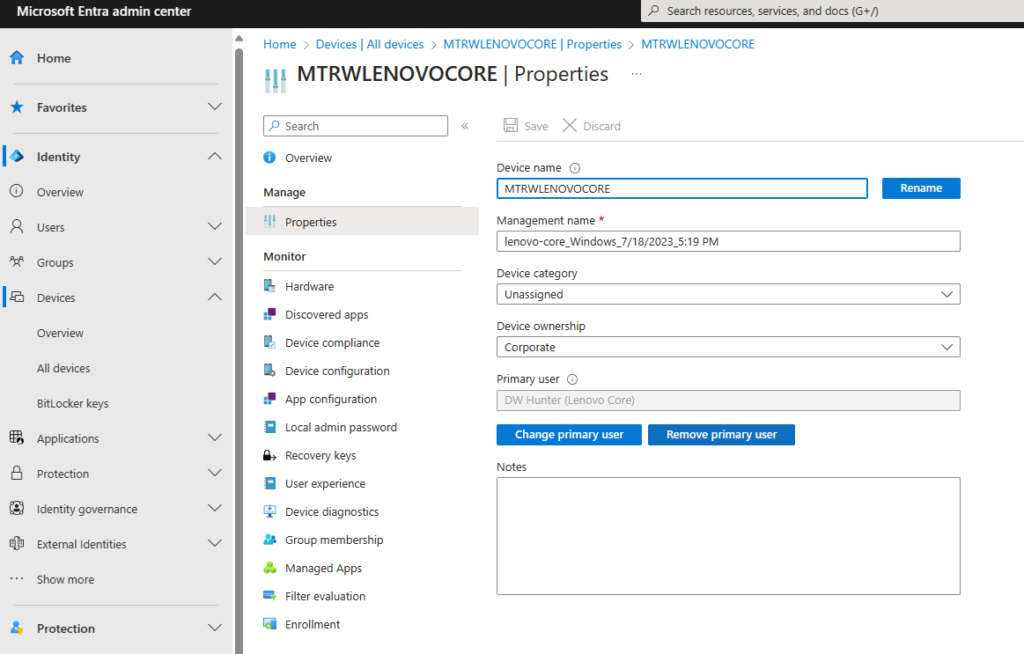
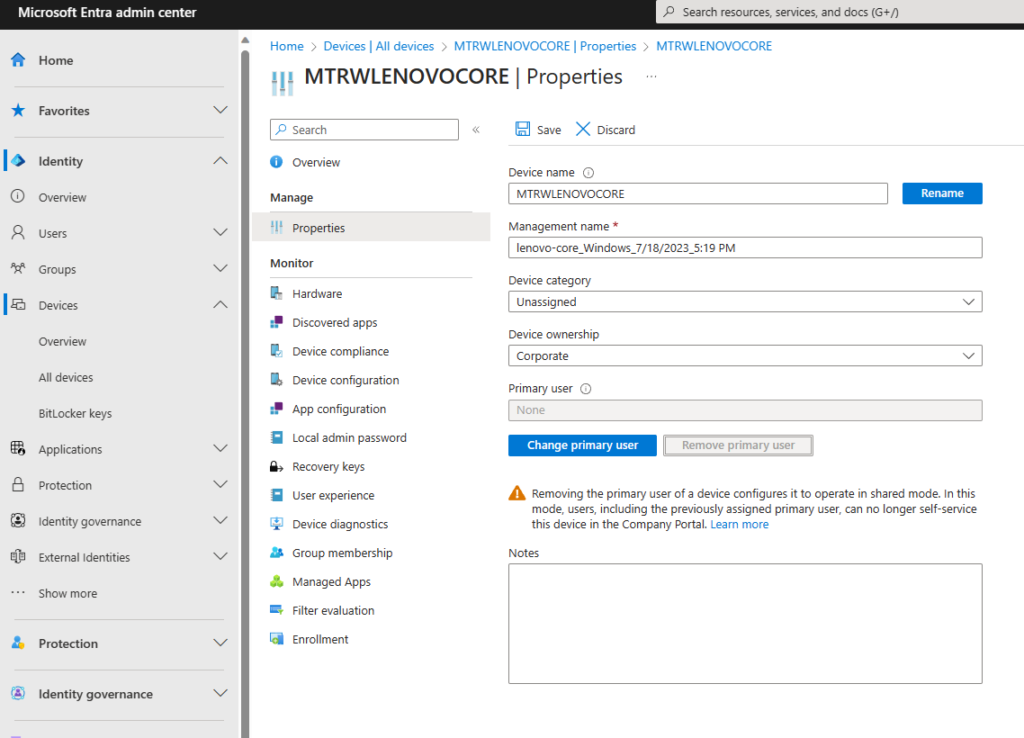
Okay, let’s check into the Dynamic Device Group
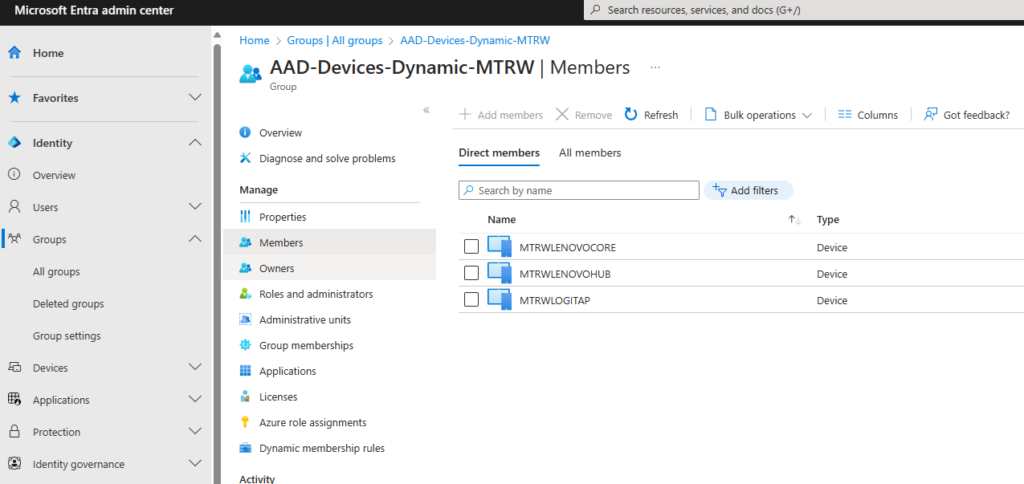
Sweet! The new device MTRWLENOVOCORE appears, that means that the Intune Enrollment / Compliance targeting should have kicked off too! Let’s head over to Intune.
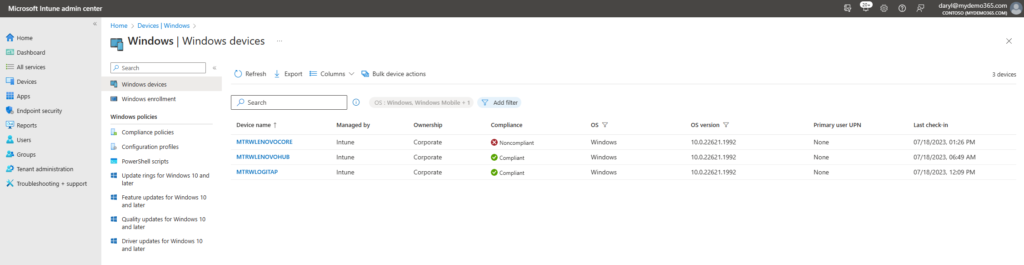
Yup. Intune knows about it. Still not compliant yet. It’s been a few mins. Let’s get a cup of coffee.
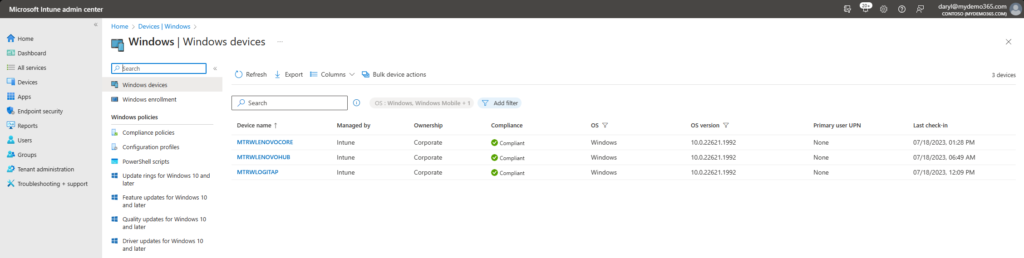
Looky there! It’s now compliant. That’s great. Now let’s make sure this device is configured to properly use lenovo-core@mydemo365.com – the resource account created and licensed for Teams Room Pro.
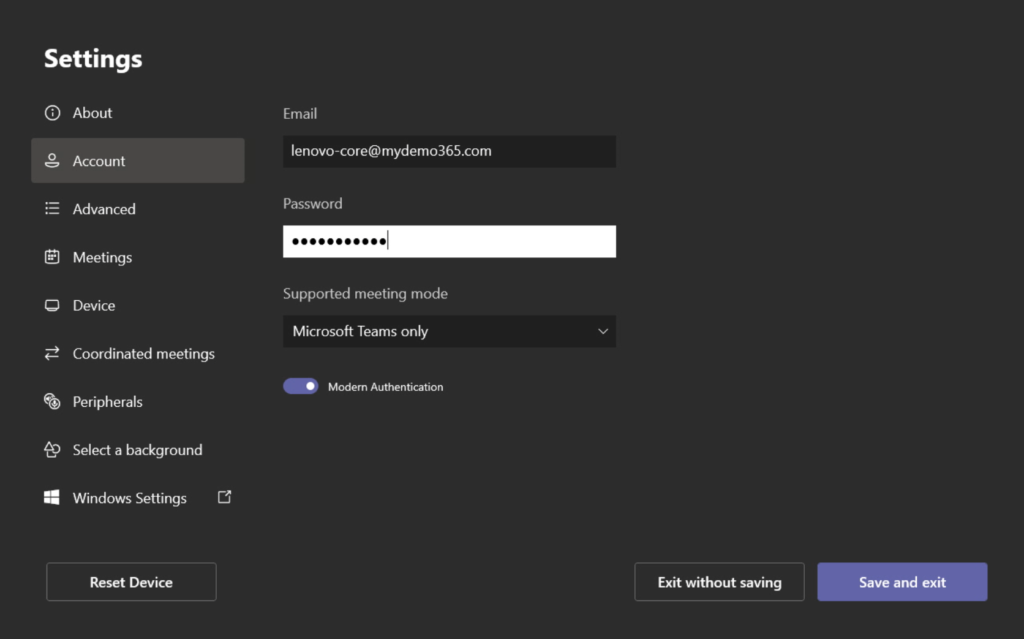
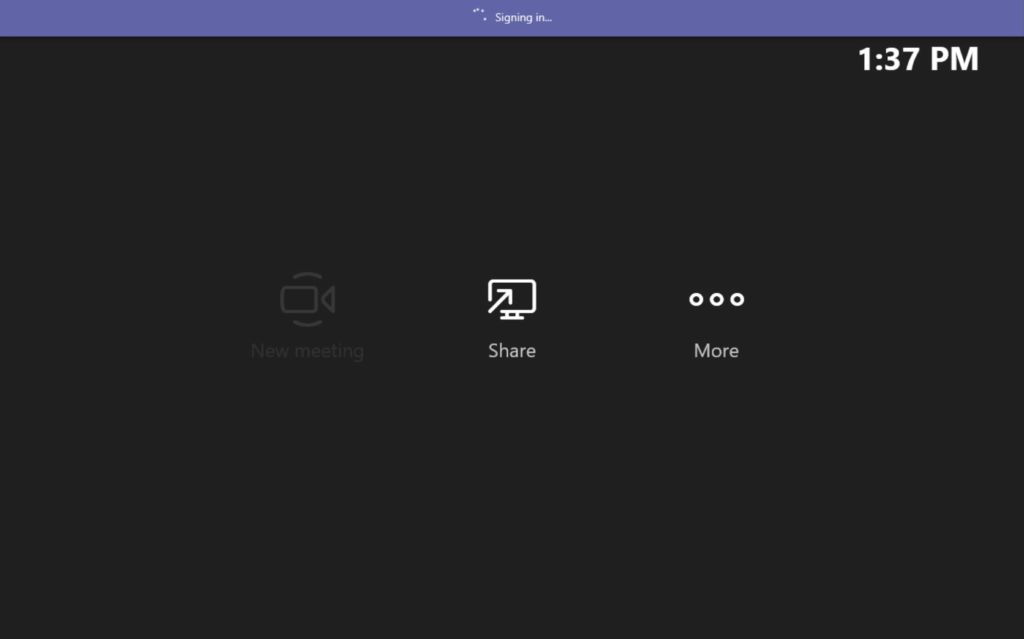
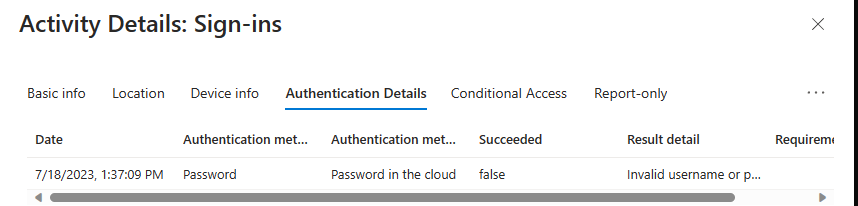
(slight pause as I fixed a password issue – dumb fingers)
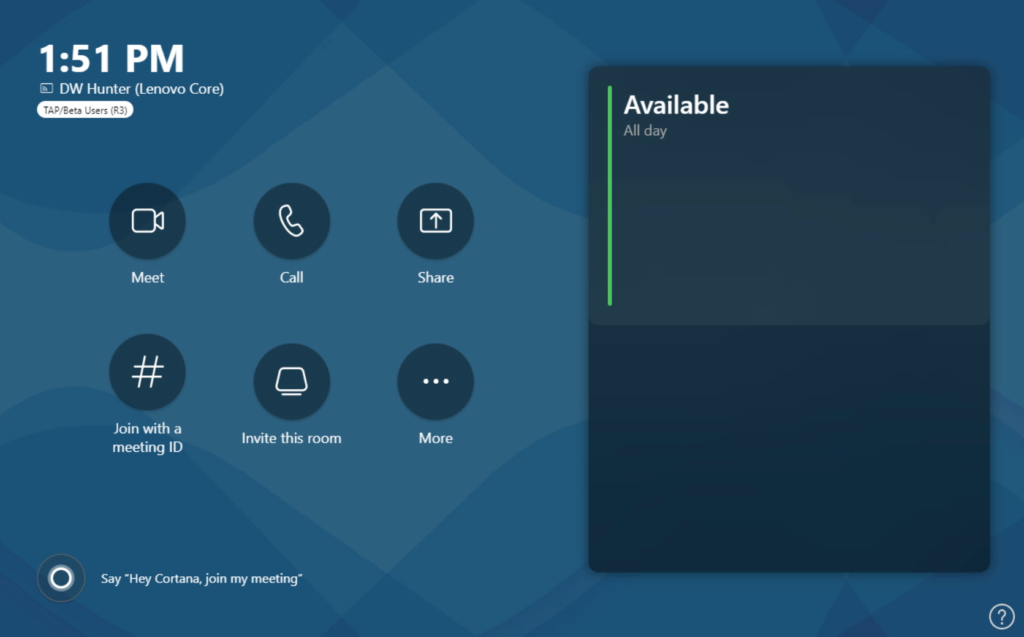
Hooray! Let’s finish our unannotated screen captures showing the conditional access success, check for IP location, and device filter exclusion to avoid the “chicken and the egg” issue I mentioned above.
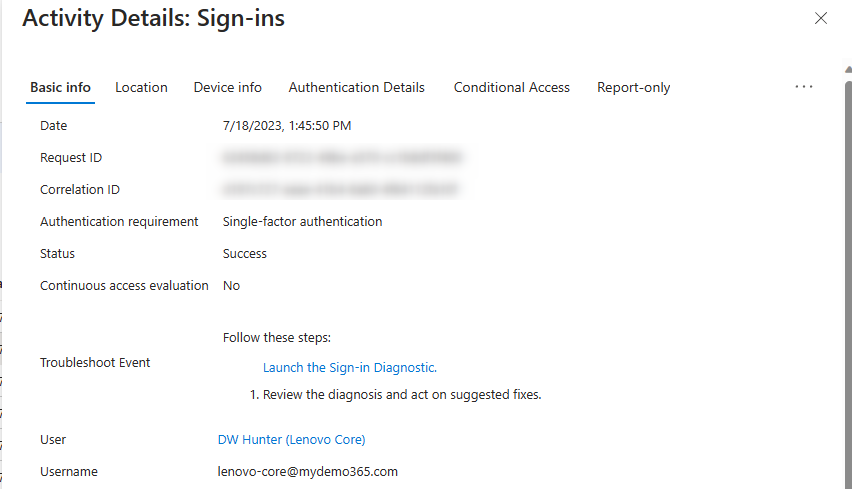
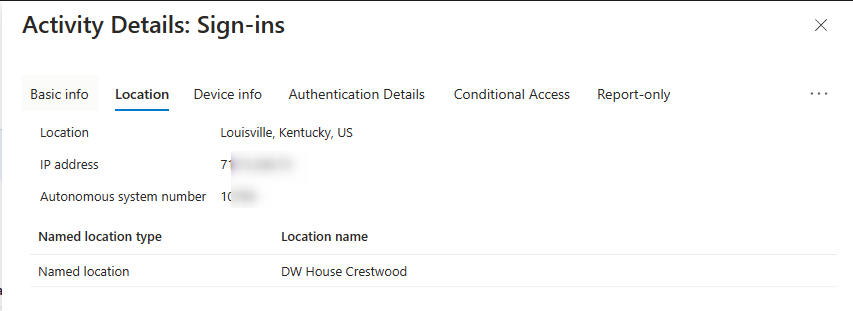
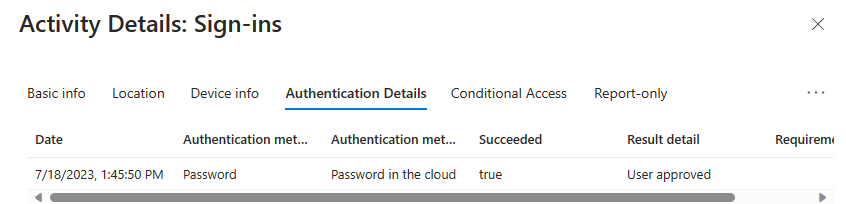
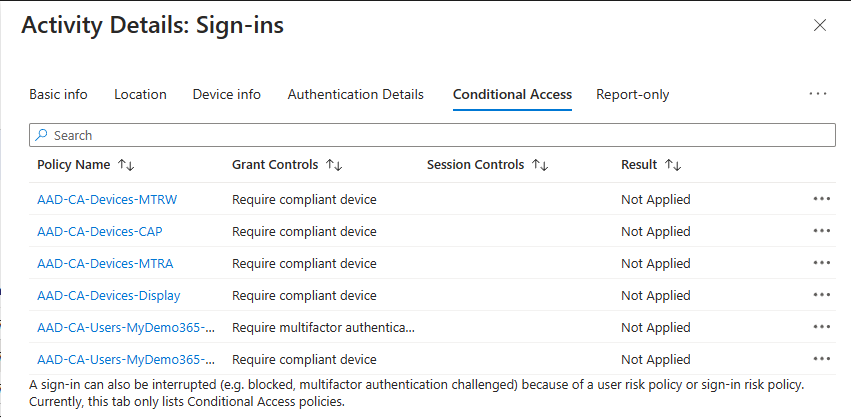
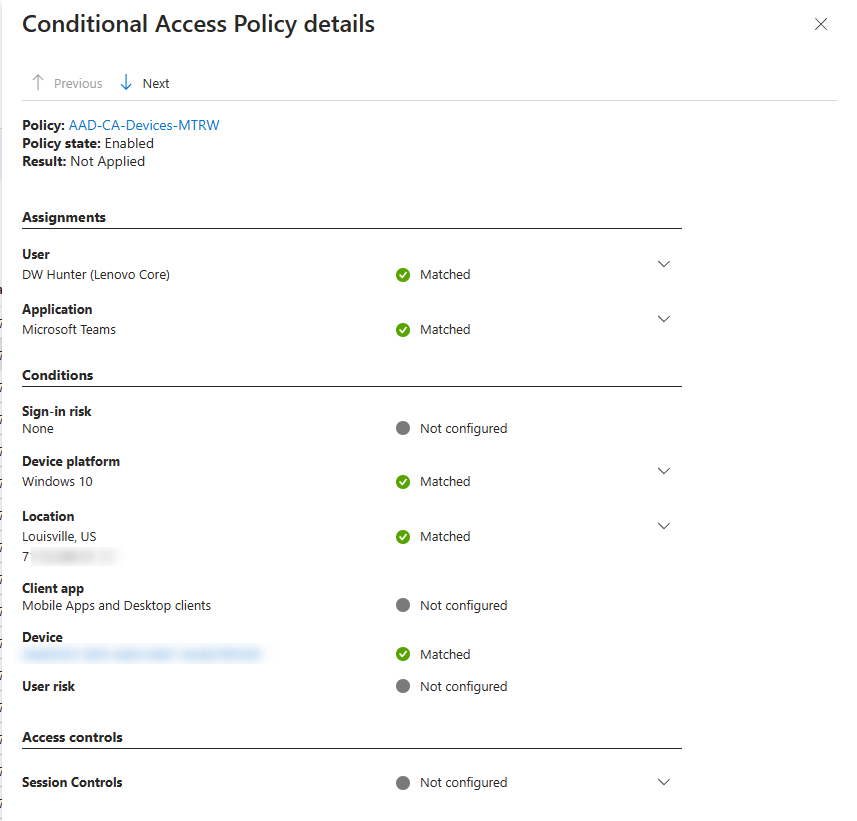
Fini
Right. There we have it. Another long post with a ton of screen captures, but, hopefully you’re starting to get inside my head a bit. Please use our Teams Devices Deployment Playbook. It’s an amazing resource! Please review the Teams Academy at https://aka.ms/teamsacademy as it contains a TON of IT Pro resources for M365 Admins & Champions just like you!