Hello again friends! One of my absolutely favorite “day jobs” is helping bridge the gaps between documentation, customer learnings and practical “how to” guides. I really appreciate the feedback y’all give so I can improve these little blogs along the way!
Today I want to tackle the subject of using Microsoft Teams Phone Devices (you know – those plastic phones that are on desks and tables and look like a pyramid with a banana on top in whiteboard drawings) and the dreaded MFA / Multi-factor authentication topic. The big blocks to discuss today will be around:
- Identity – Personal or Shared
- Licensing – Intune and/or Azure Active Directory
- Conditional Access – Compliance and/or MFA Enforcement
Identity
I covered this in a previous post, but it’s worth a refresher. As we consider which types of devices to deploy, one of the first things to consider is the type of experience to cover. Is this a personal device used by an end-user identity? Or is this a shared device covered by a resource account identity?
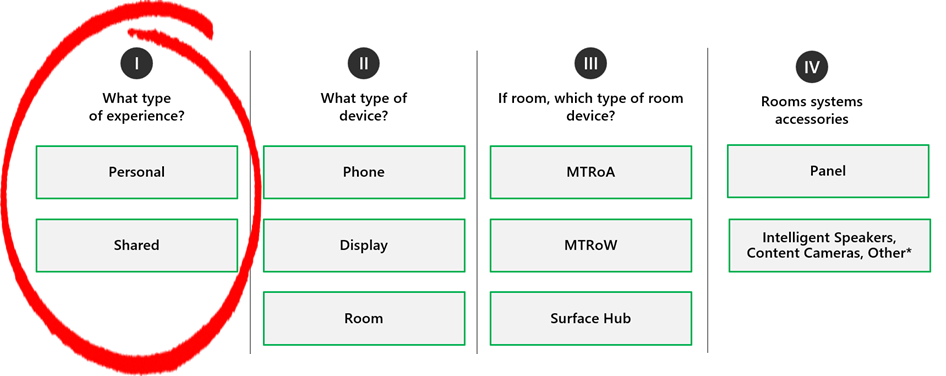
To help customers think through that, some typical scenarios can help them select devices to match. For example, is this a personal phone? Is this a common area phone? Is this maybe an executive who has a room device, but utilizes that in their personal office? Or, is this a shared room device in an office conference room? Customers need to properly create their identity to match their device experience.
There are many best practices and key things to consider in the account identity topic. Here is an excellent resource you can utilize in the Personal vs. Shared Identity conversation!
And that takes us to our first big block for today!
Licensing
I don’t want to belabor this point. You will want to audit and consider whether you need two key license types for the subject of the day: Intune and/or Azure Active Directory. If you go back to the link I shared earlier, there are two key callouts of note that are relevant in our second big block for today!

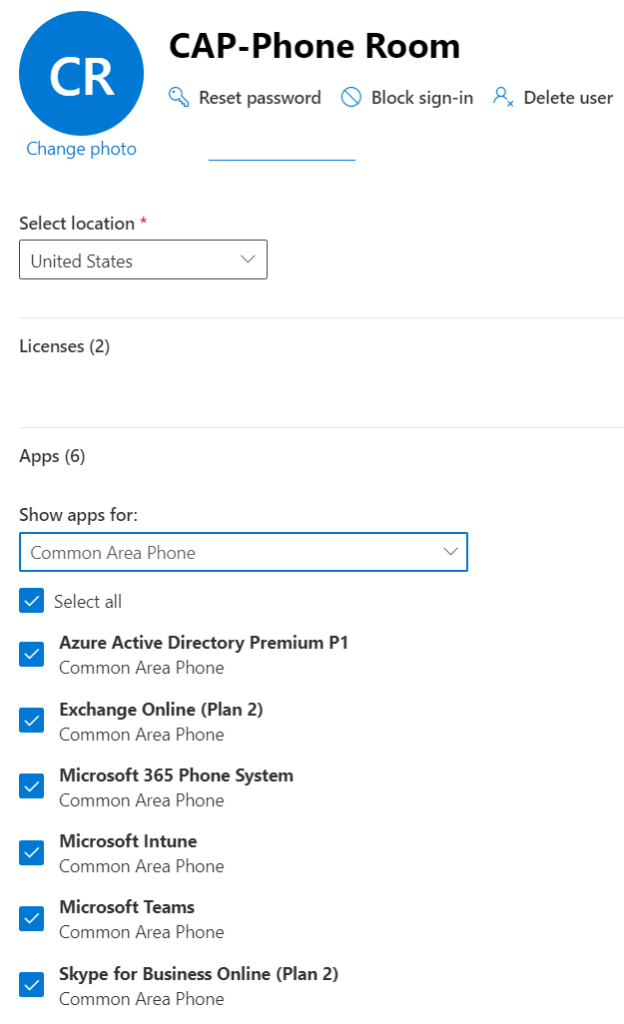
The CAP (Common Area Phone) license now INCLUDES both Azure AD Premium 1 and Intune. This is a huge thing that just happened summer 2022. You can verify this in your Microsoft 365 Admin Center like this sample CAP user below:
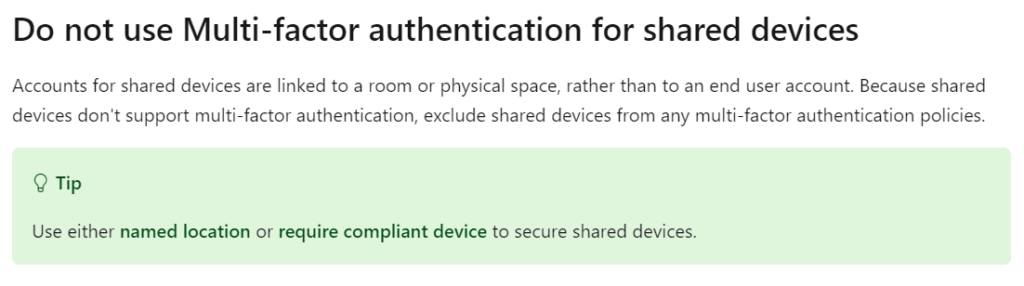
What this means is that with a shared identity type, you’ll want to utilize the Common Area Phone license license but you will NOT want to utilize MFA. See how we’re bringing this all together?
Additionally, the end-user identity might be licensed with an E3 + standalone Teams Phone license, or an E5 license bundle. That’s great. But this does NOT include either Azure AD Premium or Intune. You’ll need to cover those in another way – either with standalone licensing or a bundle SKU like M365 E3/E5 or Enterprise Mobility + Security (EMS) E3 or E5. You can verify this in your Microsoft 365 Admin Center like with this sample end-user below:
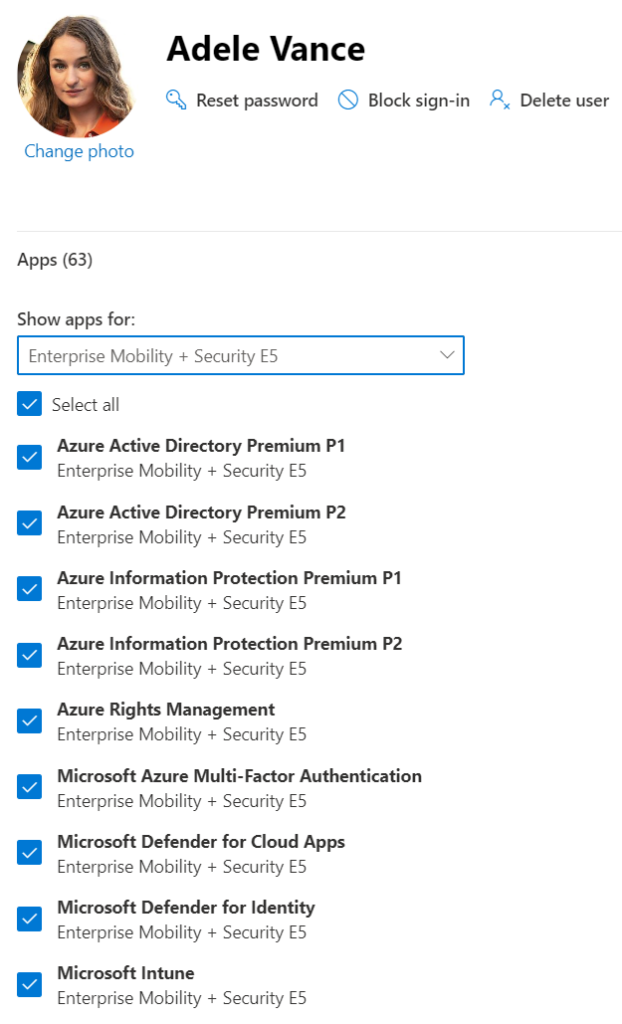
What this means is that with an end-user identity type, you’ll need to separately cover the AAD Premium and Intune license in order to utilize MFA should you choose. See how we’re bringing this all together?
Conditional Access
Okay, Let’s head over to Microsoft Endpoint Manager / Intune. We’re going to focus on Devices -> Conditional Access. You can see a few of mine below:
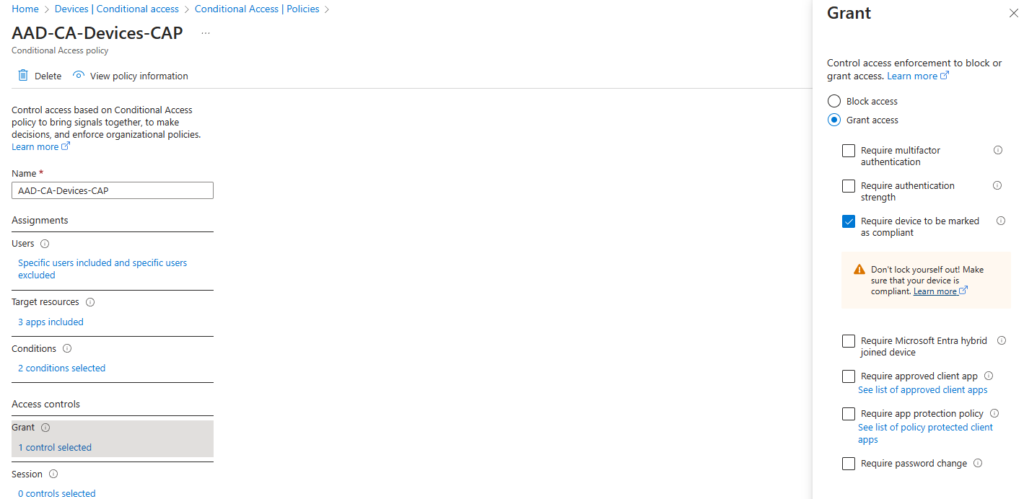
If you’ve been following along at home, you’ll probably notice two that are of note today – the CAP and MFA policy using my super clever naming convention. What would you expect to see?
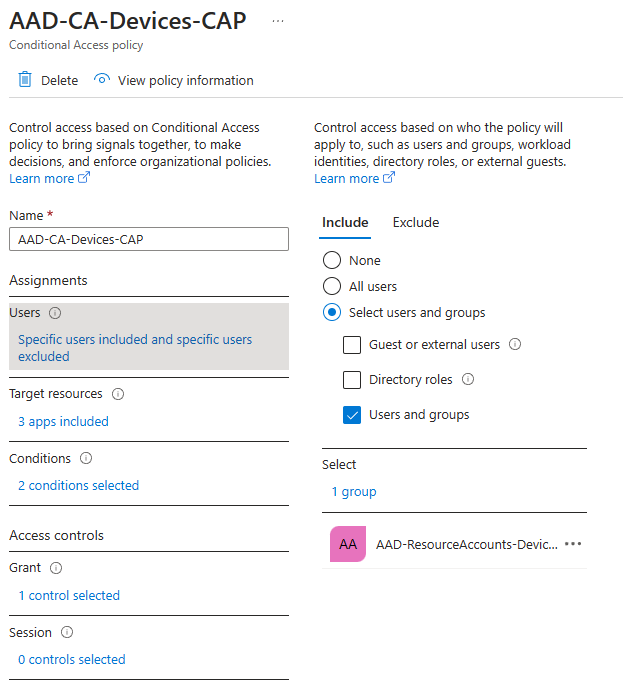
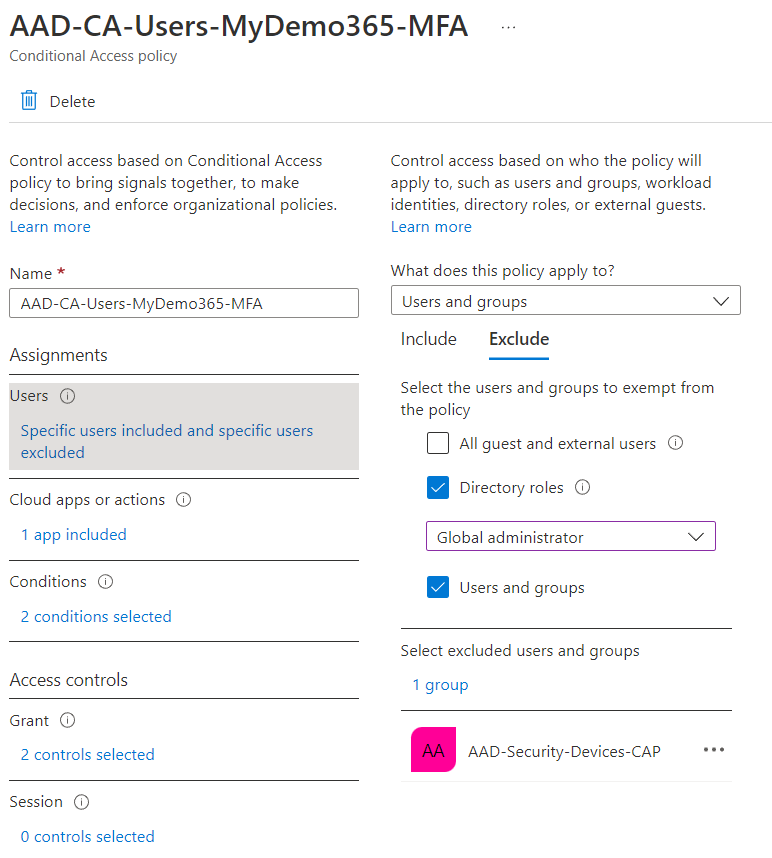
I hope you’d expect to see Azure AD Groups that contain CAP devices INCLUDED in the CAP policy and also end-users EXCLUDED here. And I bet MFA is NOT being enforced. Bingo! This is big block three for today. You’ll notice in this lab I also exclude Global Admins so I don’t get myself locked out by doing dumb things 🙂
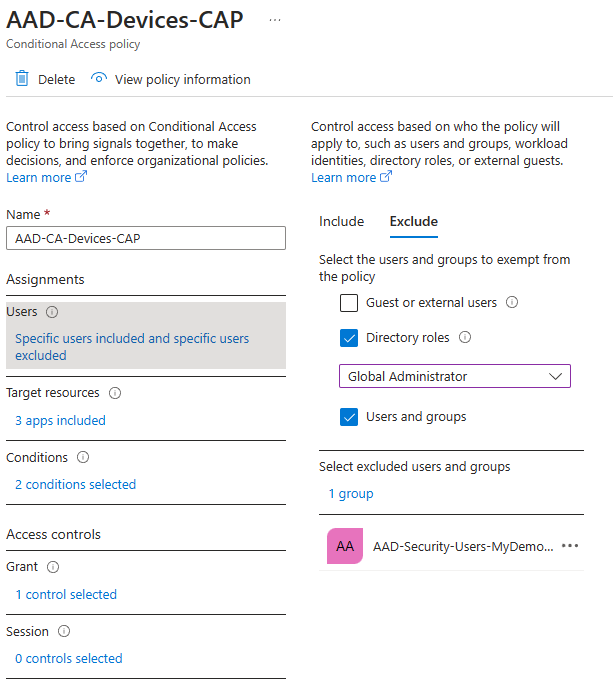
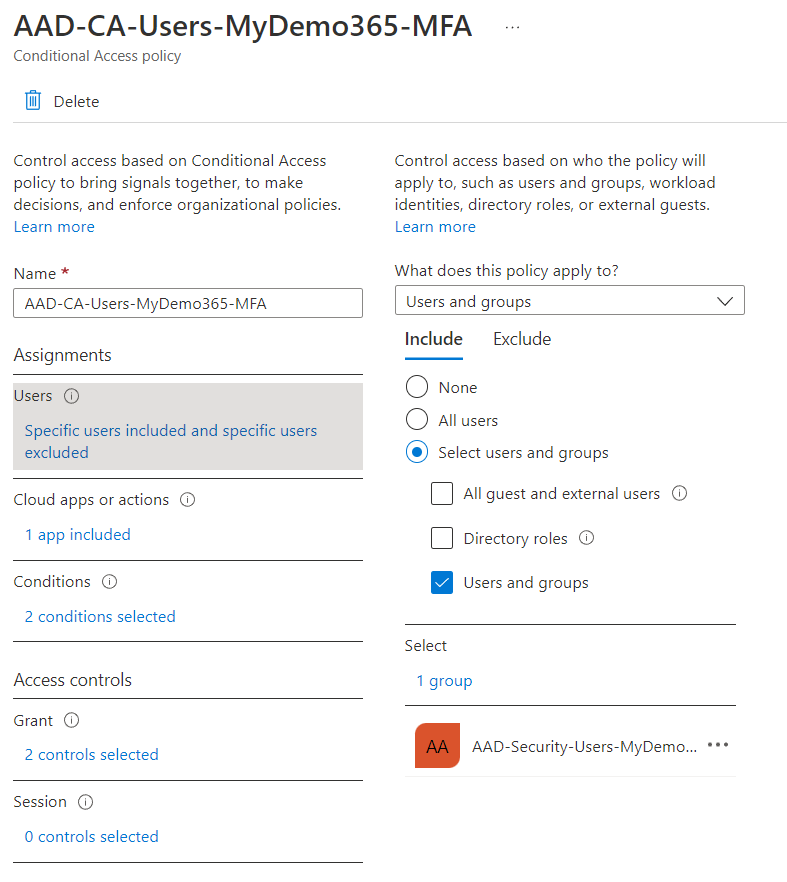
Gee DW, I guess that means the converse as well – I bet you are including Azure AD Groups that contain users INCLUDED in the MFA policy and CAP devices EXCLUDED then. And I bet you have MFA turned on! Bingo again! This is another example of big block three for today! You’re good at this!
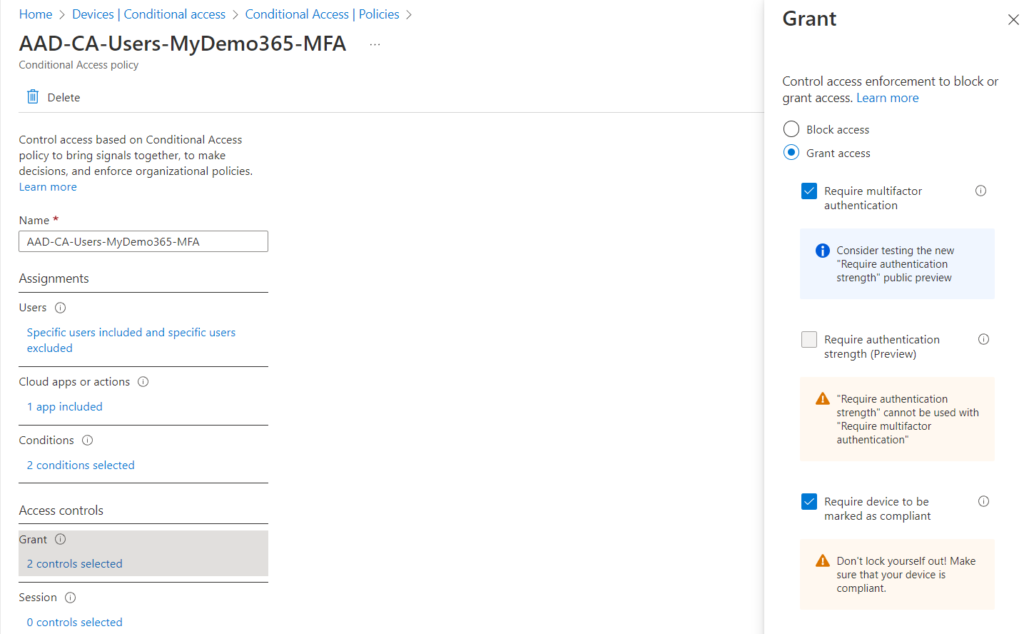
Savvy readers will notice that in both of my examples above, I am enforcing device compliance. If you scroll up that is dependent on the Intune license. So, I’m good to go. But, in your case, it’s possible you don’t care about device compliance, and only care about MFA. That’s fine. You have options. I’m demonstrating both 🙂
But What About Adele?
Right. Adele Vance. We saw above that she has all the right licensing for Compliance (Intune) and Conditional Access/MFA (Azure AD Premium). And she’s in the relevant group in the relevant policies above. But, does it work? Let’s see. We’ll try to login to my handy-dandy AudioCodes C450HD Teams Phone on my desk. We’ll utilize the device/code/pairing at https://microsoft.com/devicelogin and see. I’ve demonstrated this many times so I’ll spare you the screen shots. I get a code, I go to a website, I enter the code, I authenticate, and it magically works just like your Roku or Netflix or whatever.
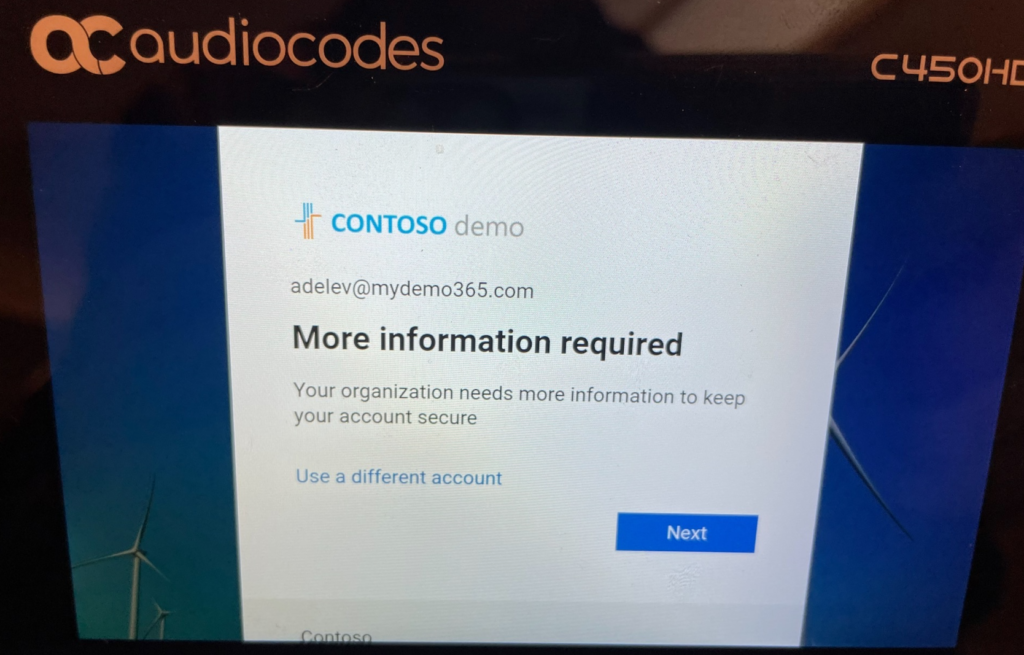
Or not. Hmm. What happened?
Oh yeah, I forgot to enable Adele Vance for MFA! Hahaha! Conditional Access is trying to enforce MFA but I didn’t do the simple MFA enablement step. My bad. Good news, I can do that directly on the phone as Adele. I’ll click Next and follow the instructions and set my mobile phone to be a text/SMS MFA provider.
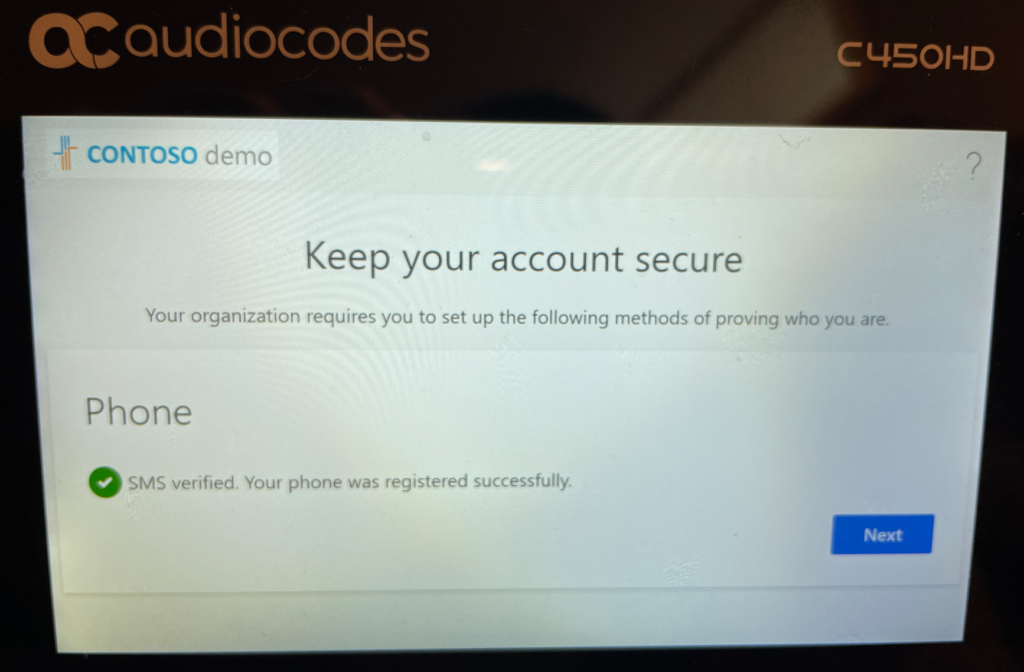
Great. And now we’ll verify it all and try again.
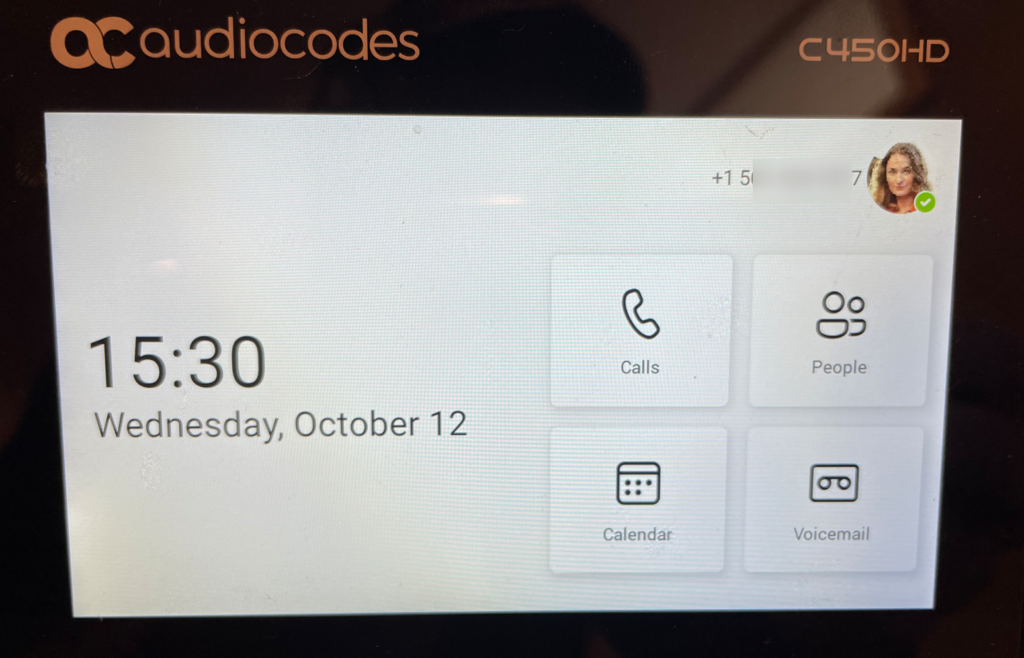
Success!
Let’s Wrap This Up
Right. You’ve done it again DW. You’ve written lots of words and given lots of pictures. Is this everything? No. This isn’t everything. I wanted to deeply cover the topic of the day which included 1) Identity, 2) Licensing and 3) Conditional Access for the MFA topic. But, don’t fret. I’m going to drop a big list of URLs that are the building blocks for all the best practices that I did not cover today but you might find useful. These will be in a soon-to-be-published Device Deployment Playbook so stay tuned for that!
- Shared / Common Area Phone
- Android Device Administrator Enabled: Click Here
- Resource Account Created: Click Here
- Password Expiration Disabled: Click Here
- Common Area Phone License Assigned: Click Here
- Phone Number Assigned: Click Here
- Adjust IP Phone Policies: Click Here
- Authentication Best Practices for Personal vs. Shared: Click Here
- AAD security group created for CAP Phones, resource account added to it: Click Here
- Intune Compliance Policy Created and Assigned to AAD Group: Click Here
- Conditional Access Configured (With IP Restrictions & Device Compliance) and Assigned to AAD Group (exclude from other existing policies): Click Here
- End-User / Personal Phone
- Review licenses assigned to users that may utilize these devices to ensure compliance with Azure AD and Intune features detailed below.
- Review Authentication Best Practices for Personal vs. Shared: Click Here
- Intune Compliance Policy Created and Assigned to AAD Group: Click Here
- Conditional Access (without IP restrictions if deployed outside office) & Device Compliance configured and Assigned to AAD Group: Click Here
Thanks again for all of your great feedback friends! Please let me know any future topics you’d love to see. I’m easy to find on all of the social mediazzzzz. Cheers!