I've had this conversation several times recently. I thought I'd take time to blog about it. It shouldn't take very long.
MYTH: You need to buy a UCC SSL Certificate in order to use Exchange 2007
What is a UCC SSL Certificate? In essence, it is a single certificate that allows multiple common names / domains – different than a "wildcard" certificate where each secured domain has the same root.
Here's what we do, and what I've done for a dozen or more Exchange 2007 installs over the last couple of years. Three easy steps 🙂
Step 1 – SSL Certificate
I buy my SSL certificates from Rapid SSL Online. Why? They are rapid, and relatively cheap. They aren't the cheapest I'm sure, but I can go from CSR to Certificate install in about 3 minutes. That's rapid and worth it to me. And, it's less than $20 for an SSL cert. So, you're gonna follow your "normal" SSL procedures to get a certificate installed on IIS to work with Exchange OWA/Outlook Anywhere/etc. – no, I'm not going to walk you through this. You can find tons of documentation out there.
Our mail server is SSL secured via the FQDN/CN of "mail01.lifechurch.tv." even though our internal domain is NOT "lifechurch.tv" – it doesn't matter. SSL Secure yourself based on the FQDN you want your OWA/Outlook Anywhere clients to use.
Step 2 – What about Auto Discover? How do I configure DNS then?
Well, this is the part that leads to the myth I believe. Many "early" Exchange 2007 adopters had to use UCC to handle the certificate issues that arose with a DNS "A" record of autodiscover.domain.com – but that is no longer the case, and hasn't been for about two years now. You can read about it on the Exchange Team Blog or in the actual technet whitepaper from October 2007.
So, what does that mean? How do I handle autodiscover without UCC?
Internal/AD DNS
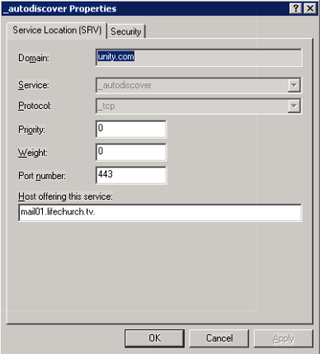
I create a DNS SRV record pointing to "mail01.lifechurch.tv" – because that's how my SSL certificate works. It looks like this:
_.autodiscover._tcp.domain.com – for port tcp443 – pointing to mail01.lifechurch.tv
External/Public DNS
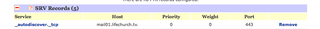
I create a similar DNS SRV record under the "lifechurch.tv" DNS zone. I use DNS Made Easy – it's awesome. Here's what it looks like:
Look familiar? It's identical to the one above it.
Step 3 – DNS Doctoring/Rewriting
This is where you may run into problems. I use a Cisco ASA Cluster for my firewall. When I create my NAT entries, I have the opportunity to rewrite the DNS resolution. Let me explain.
From my house, if I ping mail01.lifechurch.tv – I get a public 12.x.x.x address.
From inside my network, behind my firewall using DNS Doctoring – I get a 10.x.x.x address. I'm not using split brain DNS. I'm using DNS Made Easy. The Cisco ASA rewrites that. All it takes is a single firewall command.
static (Inside,Outside) 12.x.x.x 10.x.x.x 255.255.255.255 dns
That's it. That static NAT entry, combined with the "dns" attribute, will handle the rewrite for me.
I know some of you may be using Microsoft ISA, or Sonicwall, or other firewalls. I'm not sure if they will handle this rewrite for you. I've heard of people using host files to handle that, and that may work for you. But, for Cisco firewalls, it's a single command – built-in functionality.
Anyway, that's that for today's episode of Exchange 2007 UCC/SSL MYTH-busters 🙂
It works fine like that on a SonicWALL as well as long as you’re in the habit of creating a DNS loopback entry when doing your NAT rules.
Justin–
Awesome! Thanks. So, Cisco = good. Sonicwall = good. Any ISA people care to comment?
–DW
Any reason you couldn’t user split DNS to accomplish the same thing?
Dan–
User split? I assume you meant “use split” 🙂
Well, you COULD use split-brain DNS – and have “autodiscover.domain.local” on the inside and “autodiscover.domain.com” on the outside… but that would defeat the purpose of a single SSL cert… and you’d still need UCC because domain.local/domain.com are different “names”
What did you mean?
–DW
I haven’t finished setting up Exchange 2007 yet, but I actually created in my AD DNS servers a primary zone named ssl.lakeviewchurch.org and pointed it (the root record) to my internal ISA 2004 gateway IP address. On ISA I edited the HOSTS file to add a record mapping my internal Exchange IP to the same ssl.lakeviewchurch.org address. So client on LAN gets ISA IP for ssl.lakeviewchurch.org (or external ISA IP is returned by DNSMadeEasy external DNS for same request, as a subdomain with an A record).
The ISA publishing rules forward OWA traffic to ssl.lakeviewchurch.org (so the certs match up–same SSL cert installed on ISA and on the Exchange server) which ISA thinks is the LAN Exchange IP. Tada! Same name, works internally and externally for OWA, one certificate (with Exchange 2003 and, experimentally since I’m experimenting today, Exchange 2007).
Supposedly, add the autodiscover SRV records (both to the internal and external DNS servers) like you did and it should work fine.
SMTP hits the Exchange box through ISA by IP as a published server, so DNS doesn’t even come into play there.
Ok, since I am trying to do this again and my pea brain forgot you had this post and I even commented on it… 🙂 I’ll answer your question. Split DNS is necessary when (like in our situation) the INTERNAL domain and EXTERNAL domain are the same (i.e. both abcde.com). Don’t ask – I inherited it. Since my ftp and website are not onsite and http://www.abcde.com searches internal DNS first (when onsite) then I have an A record entry in my internal DNS to point www. and ftp. to external hosts. Using this same concept I can accomplish the DNS rewrite at the DNS server level instead of the gateway.
Dan–
Gotcha. Been there. Autodiscover / DNS rewriting / joy 🙂
–DW
Thanks for the information, any experience with this setup and mobile phones, ActiveSync, Windows Mobile, Mail for Exchange, etc. ?
Since this will only work with Outlook 2007 with the hotfix installed or service pack 1, I am just guessing that mobile clients might not work with this or ?
As a sidenote for cheap single name SSL certificates, I can recommend AlphaSSL as a cheap substitute for RapidSSL that is also mobile compatible.
Hey Sole–
This same setup works just fine with iPhones, Android, even Palm mobile phones. It works just fine with Exchange 2007 & also Exchange 2010. I never implemented Exchange 2007 pre-SP1 so I cannot speak to that.
I can also verify this works just fine with Outlook Anywhere, and Entourage / mail.app on MacOS.
–DW
Hi,
I’m having issues only when connecting Outlook 2007 via IMAP4 or POP3. I get a certificate error “Target name principal name is incorrect”. I did not create an SRV record, because my domain registrar could not allow it. Will this SRV record be enough and spare me from buying a UCC/SAN certificate? Thanks!
Such a detailed discussion and very useful when one need to buy an UCC certificate for their exchange server. Recently one of my client who is using godaddy ucc certificate asked me to replace the one with other low price UCC certificate.
I searched online for godaddy alternative provider and landed on this detailed comparison by Scott https://www.ssl2buy.com/wiki/ucc-exchange-ssl-certificates-comodo-vs-digicert-vs-godaddy/
I never heard about SSL2buy but it seems legit in my initial findings. Does anyone has experience with this brand? should i use their product for my client?
please suggest!