Hello friends! Another week and another post on Microsoft Teams Rooms on Windows! This week I want to cover off on an exciting new development – we now support Windows Local Administrator Password Solution (LAPS) on Teams Rooms on Windows. LAPS is a solution that automatically generates a random and complex password for the local administrator account on each Entra joined Windows device and stores it securely in Entra or Active Directory. This password can be periodically changed/rotated according to the configured policy. In short – we’ve heard from many of you where this password rotation is needed for the local administrator account on the Teams Rooms device. We’ve delivered. You can read more in our Learn Article on the subject. I’ll do my usual “boots on the ground” approach of how to set this up in your environment.
Before We Get Started
You should read the Learn Article. It covers off of important considerations like how you should utilize Entra ID where possible. Also you should note these Teams Rooms devices must be Entra joined or Hybrid Entra Joined and managed by Intune before moving forward.
IOW – be sure to check with your OEM. Any peripherals or endpoints that connect to the Teams Rooms on Windows device using the local administrator credentials will lose connection upon reboot or password change. Do your homework!
Entra Configuration
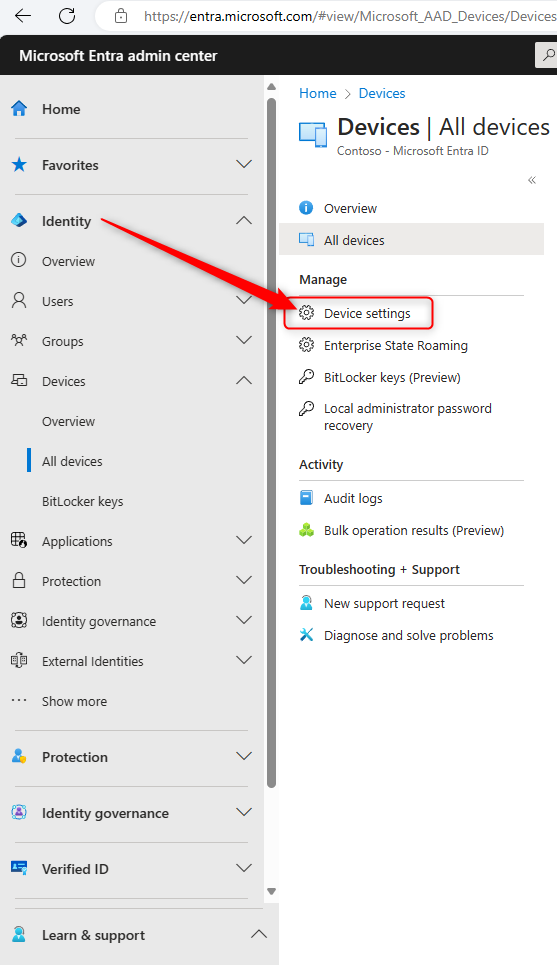
To enable LAPS in Entra ID, we’ll do that in the Entra Identity admin console at https://entra.microsoft.com and navigate to Identity -> Devices -> All Devices and choose Device Settings
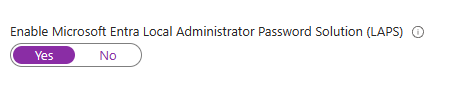
Move the slider for Enable Microsoft Entra Local Administrator Password Solution (LAPS) to Yes
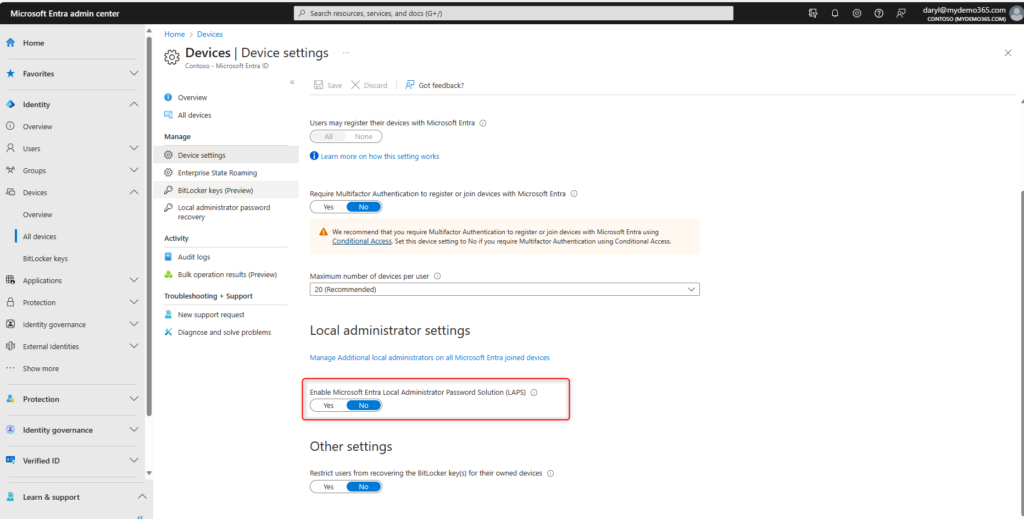
Click Save and let this setting take effect!
Intune Configuration
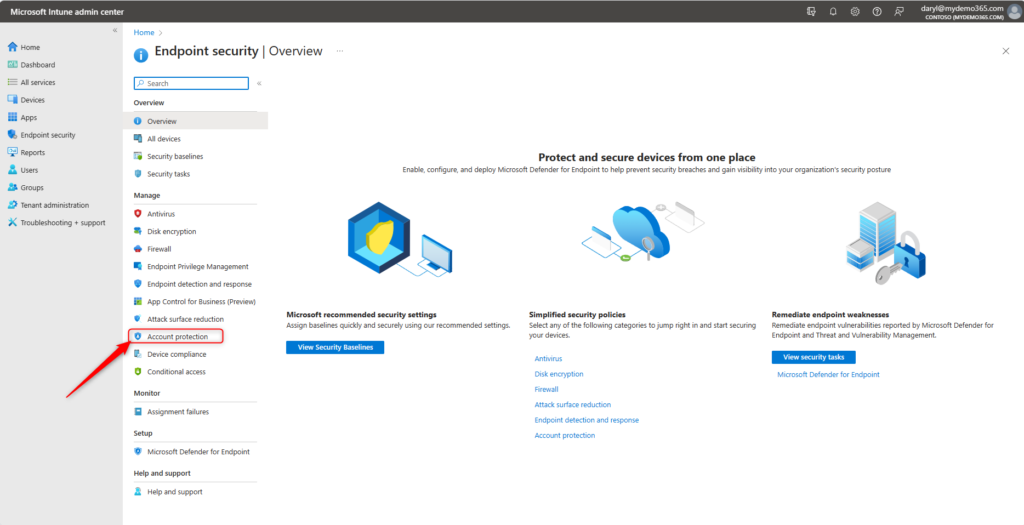
To create and assign the LAPS policy in Intune, start at the Intune Admin Center at https://intune.microsoft.com. You’ll want to navigate to Endpoint Security -> Account protection.
Create a new policy!
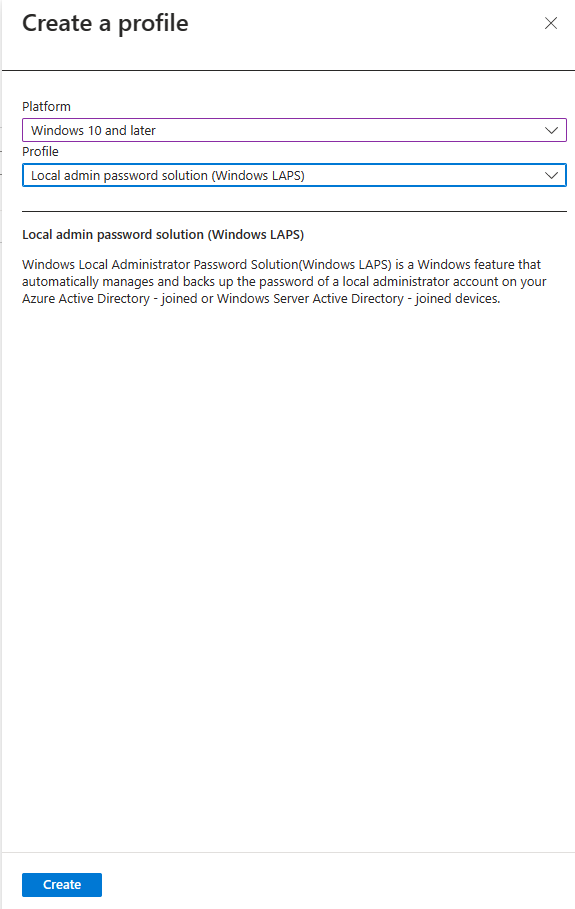
For platform, select Windows 10 and later and profile LAPS. Click Create.
Now, let’s run through the policy settings that are important to note. Start with a useful name/description.
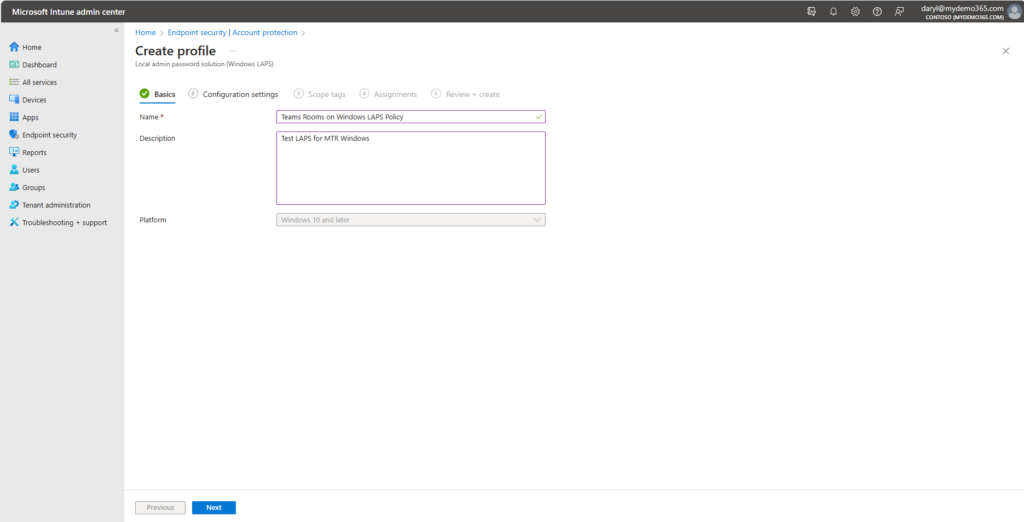
Select the option for Backup Directory to point to Azure AD only, toggle Password Age Days and make your choice (I chose 90), Toggle Administrator account name and have it match the local administrator account (For MTR Windows, it’s Admin), select the desired password complexity option, toggle password length and pick your desired length (I chose 14).
Click Next twice if you don’t use scope tags (which I don’t). But if you do use them, do that here.
Now scope to your desired group of devices. For me, if you recall some of my earlier posts, I use the AAD-Devices-Dynamic-MTRW group as the one which contains the Teams Rooms on Windows devices.
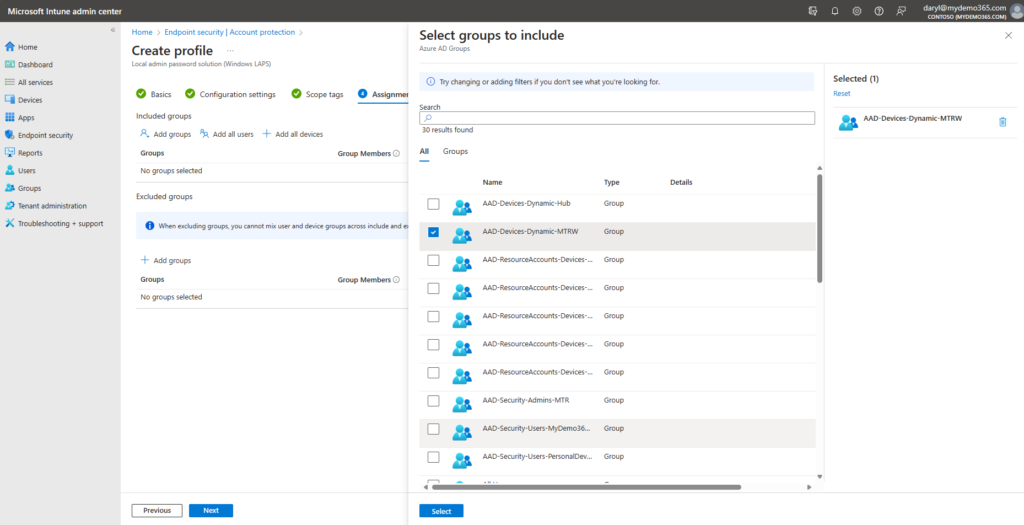
Validate those settings and click Next.
Everything look good? If so, click create.

Now, let it sit. It will take up to an hour for everything to sync up and for the magic to happen. Go eat dinner. Or take a walk. Maybe play some pickleball. Then come back.
LAPS Operations
First of all, let’s validate this policy has properly been assigned to my scoped devices. In my case, these area Lenovo Core and Logi TAP Teams Rooms on Windows device.
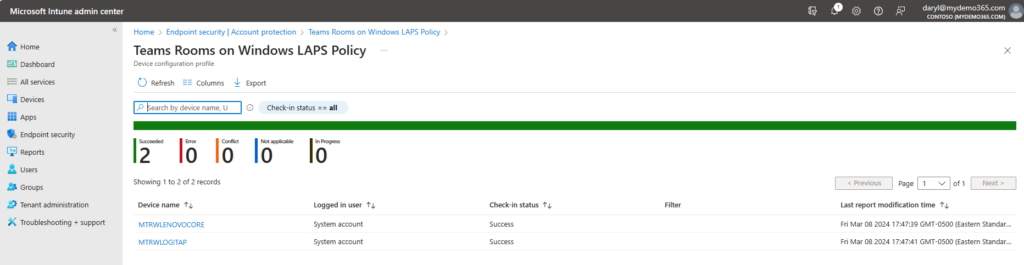
Sweet. All good. Now, what if I needed to retrieve the local administrator password? Well, assuming I have the right scoped roles, I can do that from Entra via the Admin Center at https://entra.microsoft.com and navigate to Identity -> Devices -> All Devices and choose Local Administrator Password Recovery.
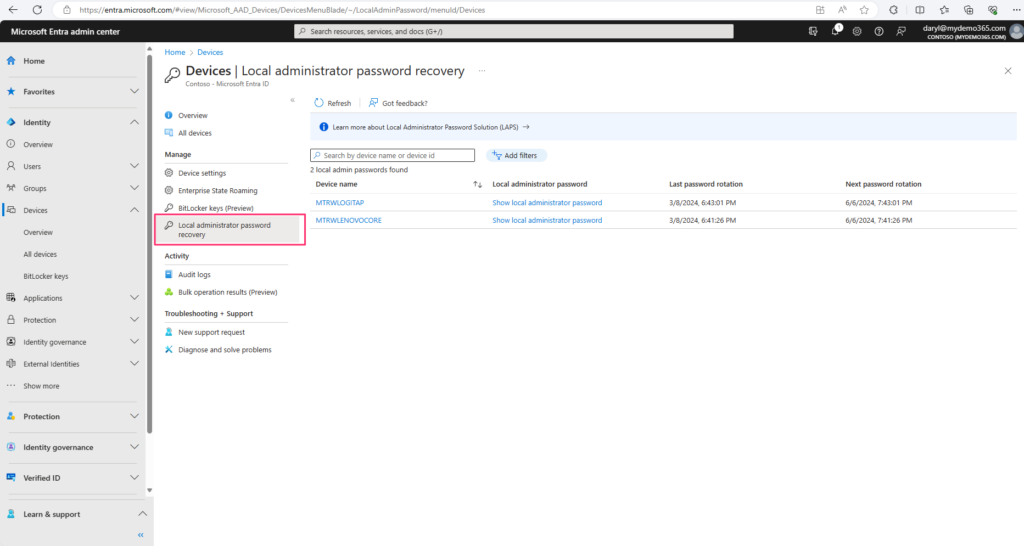
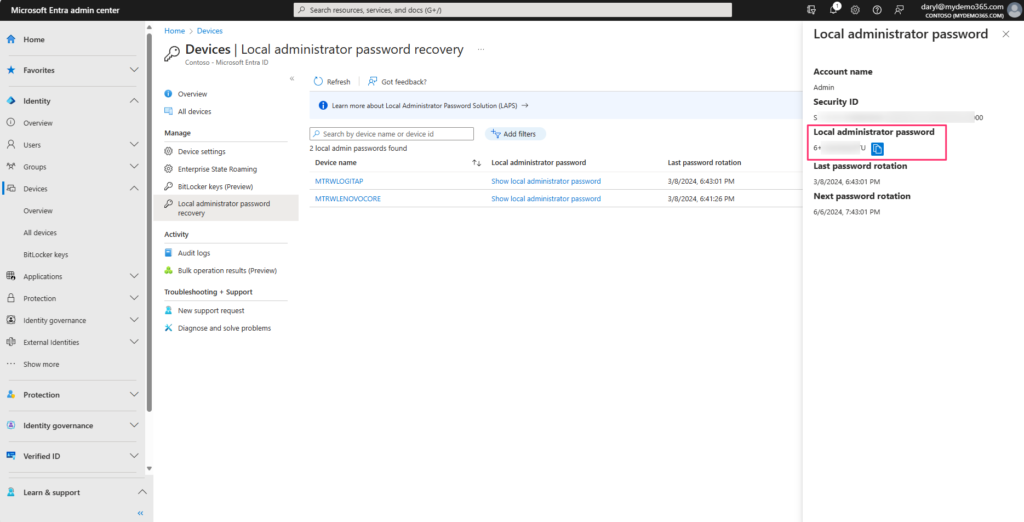
If I pick one of those, I can see the (blurred in my image) local administrator password and use it as needed. I can also see when it was last changed/rotated and when it rotates again next time.
Useful Audit Logs
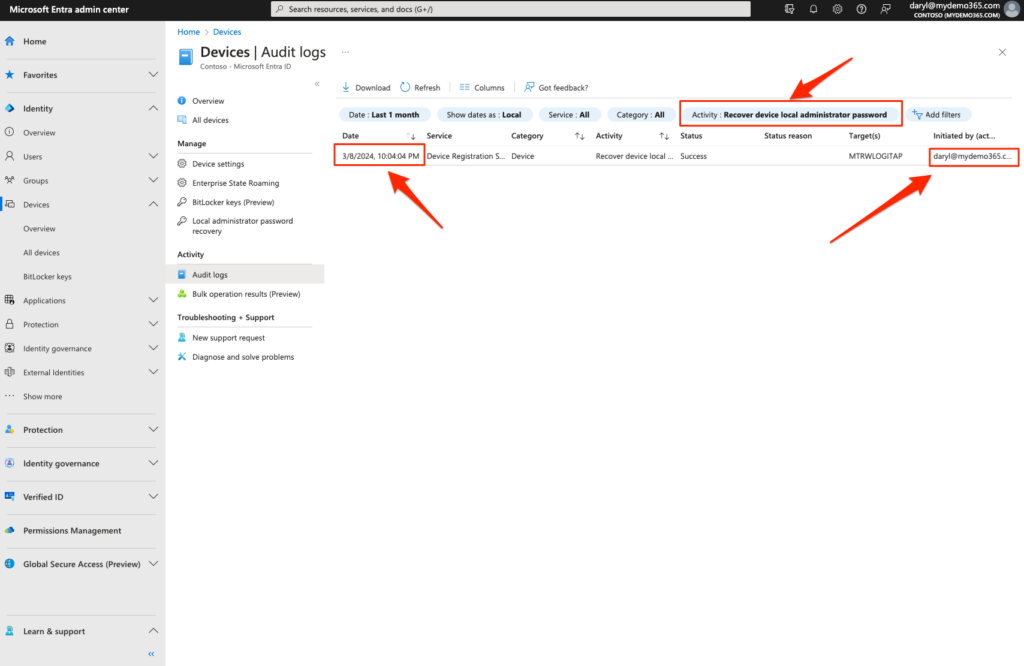
To review the audit logs in Entra, let’s go back to Entra at https://entra.microsoft.com and navigate to Identity -> Devices -> All Devices and select Audit Logs
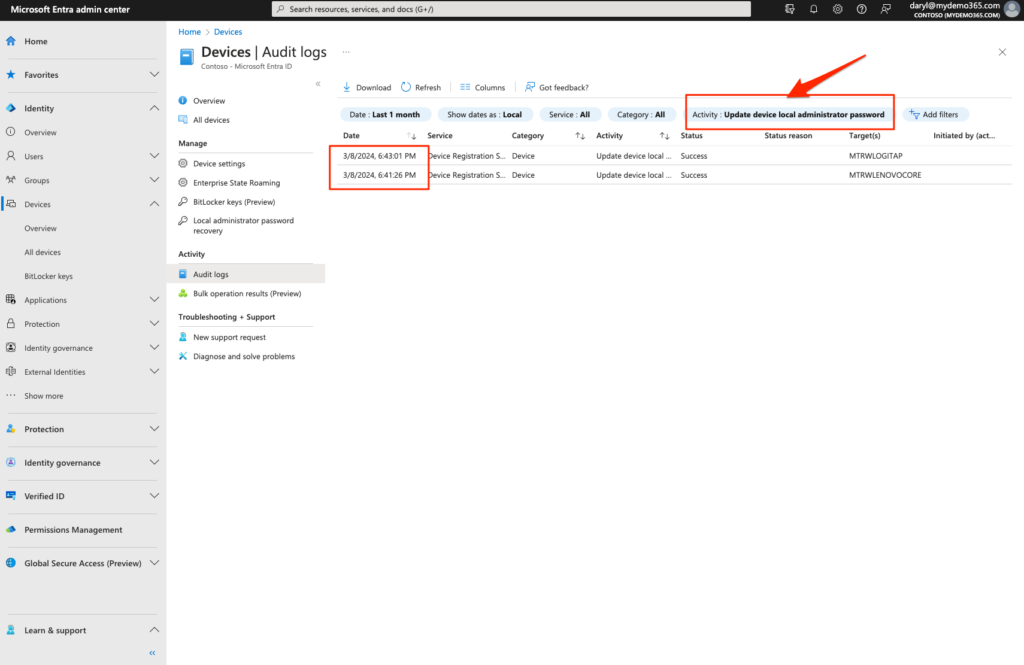
When that comes up, let’s filter against Update device local administrator password to see when changes were made across all the devices.
And what if I wanted to see who looked at a one of these passwords? Same place. Different filter. Choose the Recover device local administrator password filter and you can see that sketchy “Daryl guy” looked at the password for the MTRWLOGITAP device.
Wrap Up
There you have it! LAPS is a Windows feature that enhances both the security and management of local administrator passwords for Teams Rooms on Windows devices. I hope you’ve found this helpful! And, here are a set of adjacent useful articles you might enjoy:
- Windows LAPS Documentation Windows LAPS overview | Microsoft Learn
- Manage Windows LAPS with Microsoft Intune Policies Manage Windows LAPS with Microsoft Intune policies | Microsoft Learn
- Windows Local Administrator Password Solution in Microsoft Entra ID Manage Windows LAPS with Microsoft Intune policies | Microsoft Learn
- LAPS CSP Manage Windows LAPS with Microsoft Intune policies | Microsoft Learn