//UPDATED 8-19-2010 To Add Dell 62xx Config At Far Bottom//
Welcome back! As I posted last time, one of my latest projects has been to change all the login / enable passwords for our various Cisco routers & switches. I chose to go RADIUS + Server 2008 for that project and you can read more about that here.
We also have a good number of Dell PowerConnect (3xxx / 5xxx / 6xxx) devices too. Since RADIUS worked on the Ciscos, surely I can take what I learned and translate that to Dell, right? Let's try.
Dell CLI Config
**note** this is confirmed to work on Dell 5224 Switches
So – let's get a local username – so if RADIUS is down we can still logon the device.
username <username> access-level 15
username <username> password 7 013B072C5A26070B2475411C350A18192218313A6A671F1A1B
Great – now we'll add the appropriate AAA stuff
authentication login radius local
authentication enable radius local
Then the RADIUS server info
radius-server host <ip address>
radius-server key <SharedKeyHere>
That's it. Nothing else to do on the Dell CLI for me.
**note** this is slightly different to make work on Dell 3448 Switches
username <username> password CleverPasswordHere level 15
radius-server host <ip address> key <SharedKeyHere>
aaa authentication login <radius profile name> radius local line
aaa authentication enable <radius profile name> radius
line telnet
login authentication <radius profile name>
Windows Server 2008 NPS Config
As before, the Windows Server 2008 NPS Config for RADIUS was a little tricky. The good news is that the "heavy lifting" was done when this was setup for Cisco / RADIUS. Let's get going.
Let's start by creating some clients – these will be our various Dell devices. Let's go to NPS, expand on RADIUS Clients and Servers, right-click on RADIUS clients and choose new.
Great – now…
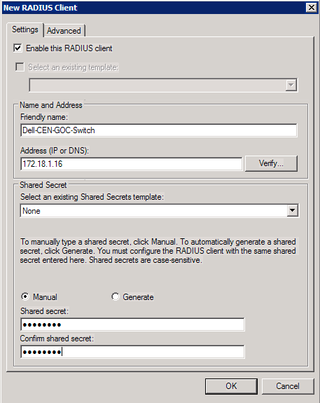
Here's some useful info. Notice I started with the "Friendly name" of "Dell-" that will be important later. The shared secret is the same as I entered in the CLI above and they need to match. Click on the advanced tab.
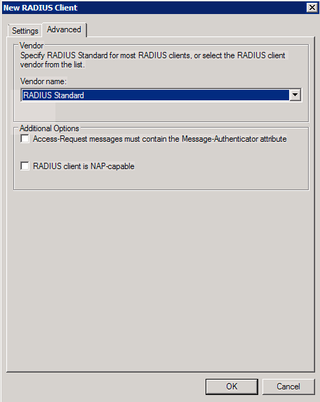
Notice that we're using "RADIUS Standard" here. There's no option for "Dell" and that's fine. Click OK.
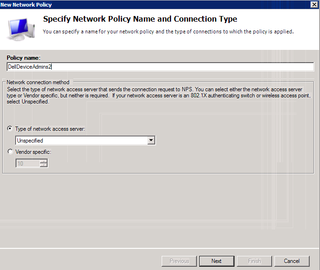
Head back to NPS. Right-click on Network Policies and choose New.
Great, let's go …
Give your policy a useful name. Unspecified is fine. Click Next.
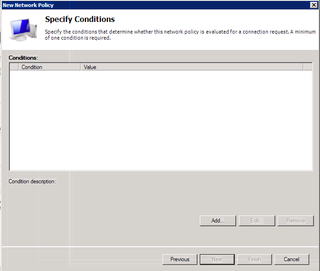
Time to add some conditions for access. Click Add.
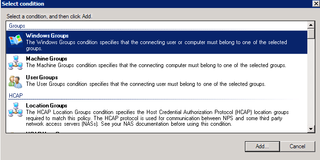
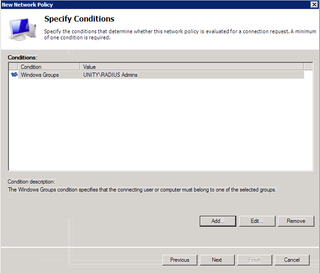
We want AD (Windows Groups) authentication. Highlight that and click Add.
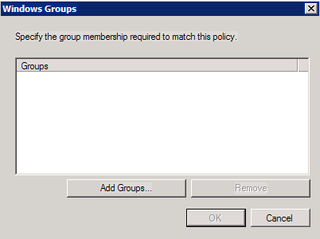
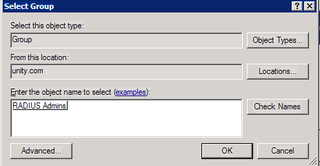
Click Add Groups – we're going to add our "RADIUS Admins" here.
Yup. Click OK and OK again.
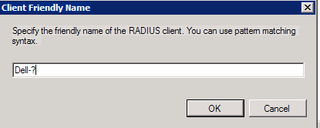
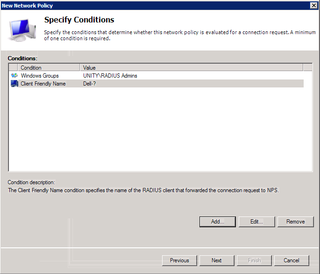
Okay. Now, let's identify the various RADIUS Clients that are important here. Let's get the ones that start with "Dell-" so click Add.
What we want is "Client Friendly Name" – Click Add.
Great. We want anything starting with "Dell-" so – "Dell-?" works (so does Dell-*). Click OK.
Yup. Great. Click Next.
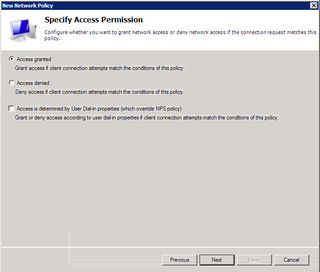
Yes please. Access Granted. Click Next.
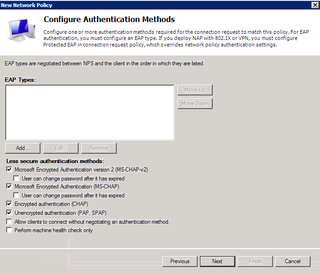
Make sure you've got PAP checked. Next. No need to read help.
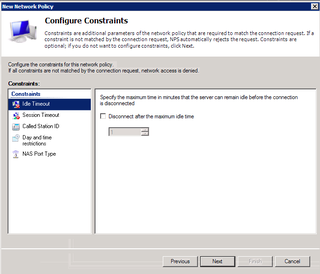
No constraints to deal with. Click Next.
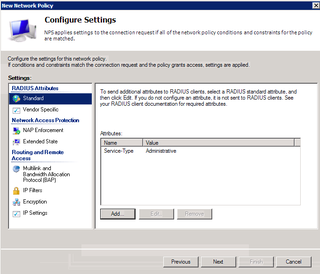
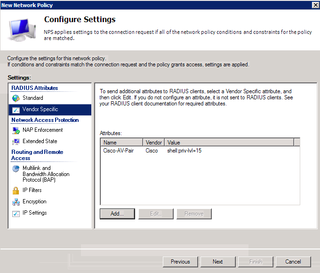
Okay. Pay attention here. This is DIFFERENT than the Cisco RADIUS thing we've done in the past. First of all, remove PPP and framed from the attributes and click Add.
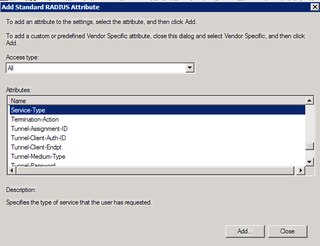
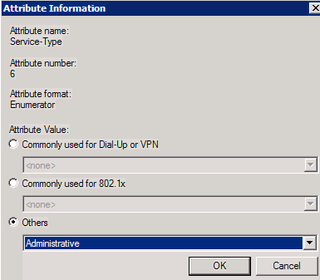
Choose Service-Type and then click Add.
Choose Administrative here. Before we chose "Login" (Cisco RADIUS) – but this time we choose Administrative. Why? Because I said so :) No, really because this blog post said so. Click OK.
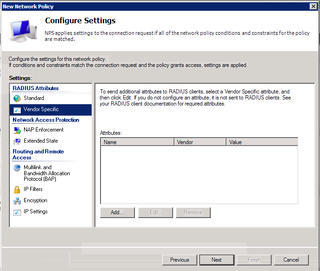
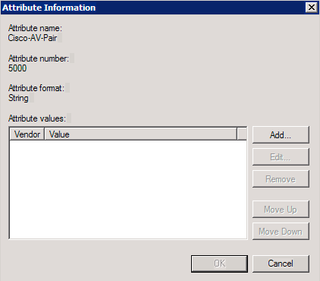
That's all there. Now, click on Vendor Specific.
Click Add.
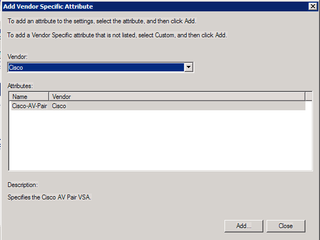
Choose Cisco (Vendor) and Cisco-AV-Pair (Attribute) and click Add. Why do you do this? We're talking about Dell switches here. Well, this attribute is what is used by Dell switches to assign privilege level. Odd I know. Go with it. Click Add.
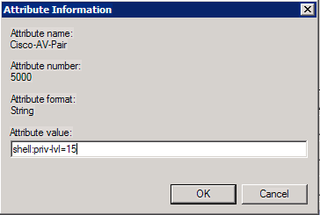
Yup. We want a string. Click Add.
There ya go. This string is what gives us "privilege 15" – or – administrative access on the Dell gear. Click OK. Click OK again. Click Close.
Looks good. I used default values for all the rest of the NAP / RRA stuff. Nothing to see there. Click next and move along.
Verify and click Finish.
Let's Test
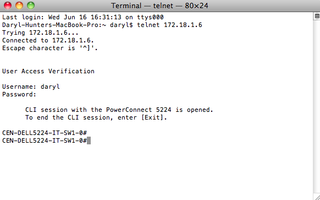
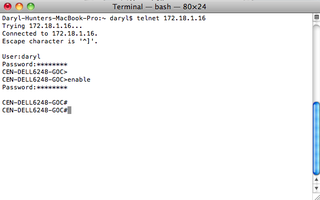
Now, let's test this sucker! Drop to a terminal and try to telnet to that Dell switch.
Awesome! We're in!
That's that. So, RADIUS is done for Dell PowerConnect 5xxx/3xxx switches. Everything is setup and tested fine. I hope that helps someone else. Let me know if it does!
**NOTE** after much head banging, this has been resolved for the Dell PowerConnect 62xx family of switches and also the M6220, M6348, M8024, 8024F, 8024 (mentioned in the comments).
Dell CLI Config
The CLI config for the Dell 6248 is similar to the others. It looks like this:
First we need a local username – so if RADIUS is down we can still login
username <username> password 013B072C5A26070B2475411C350A18192218313A6A671F1A1B level 15 encrypted
Great – now we'll add the appropriate AAA stuff
aaa authentication login <group name> radius local
aaa authentication enable <group name> radius enable none
What those do is give an "order" to the login options – radius first
Then – the RADIUS server info
radius-server host <ip address>
usage login
key <shared key name?
Finally – enable RADIUS for your mgmt login (for us – that's telnet)
line telnet
login authentication <group name>
enable authentication <group name>
That's it. CLI done.
Server 2008 Config
Nothing needs adjusted for Server 2008 NPS. All that is the same as above.
However, this series/family of Dell PowerConnect switches use a special RADIUS username called $enab15$ for privileged exec (administrator) mode. Let's walk through that.
Open ADUC on your Server 2008 machine and create a new user with the username of $enab15$. Mine has the "friendly" name of Dell Enable. The password you give this account will match your "enable" password on the Dell CLI. I also made this user a member of the appropriate "Radius Admins" group mentioned above in the NPS setup.
Basically, how this works, when you telnet to a Dell 6248, it uses RADIUS for the authentication, and then uses the $enab15$ username for the authorization. You login, then type in enable, and then type in the enable/$enab15$ password for administrative access.
Let's Test
Drop to a terminal program and attempt to telnet to one of the devices in question…
If you noticed, this is slightly different than above. On the 3xxx/5xxx series in the first part of this post, you were automatically placed into administrative mode (the # prompt). On the 6xxx series, you have to utilize the "enable" functionality coupled with the $enab15$ user.
GOTCHA – I ran into a problem with the v2.0.0.12 version of the firmware. That version would never actually allow the "enable" username to work. It just wasn't an option. You could login (authenticate) via RADIUS, but there was no way to properly get authorized to do anything via CLI. I actually downgraded to v1.0.2.6 here and things were great. I will address this and test better/newer versions of the firmware, but to get through this project the downgrade worked for us.
So, the two issues I had with the 62xx series at first were 1) firmware bug and 2) not understanding the $enab15$ username needs.
Hope that helps someone!
That is awesome information… Thanks for sharing.
Regarding the 62xx issue. (this also applies to the Dell M6220, M6348, M8024, 8024F, 8024)
No issues with their switch configuration.
However, they did authenticate, but not administratively. I believe their root issue is with the RADIUS server user configuration. They are using Cisco-AV-Pairs to configure the user’s administrative rights (shell:priv-lvl=15). These devices do not support Cisco-AV-Pairs. Instead you must use ‘Service-Type = Administrative’ to assign a user admin level 15 rights (or ‘Service-Type = NAS Prompt’ for user level 1). We had our network device vendor clarify this in their Configuration Guide, but Cisco-AV-Pairs do work with other Dell products, so this invites confusion.
BH – thanks for stopping by.
I cannot get this to work with “Service-Type = Administrative” giving a user admin level 15 rights.
It authenticates with the > prompt (and not the # prompt) which means the user is not given level 15
I’ve spent many weeks on it and just cannot get a 62xx to get level 15 access.
I’ve tried ST = Login and ST = Administrative both with and without the Cisco-AV-Pairs string text.
Can you reference any specific setup – including screen shots – that successfully has a 62xx and Server 2008 NPS (not Server 2003 IAS) talking RADIUS? I cannot find one. My calls to Dell support have not been helpful either.
Thanks,
–DW
With my work on implementing RADIUS on the Dell 5224 switch, I have found that the switch has an 8-character password limitation (as do the Dell 32xx series switches).
With the default password complexity requirements in Active Directory, if your user passwords are over 8 characters long you will get authentication failures as the 5224 will truncate the passwords down to 8 digits. You will see the authentication failure in the system event log as “username/password incorrect” (or something to that effect).
Either you have to change the password complexity requirements in AD to suit the 5224’s 8-character password limitation (highly undesirable), or just realize the 5224 is an old dinosaur and should be replaced with something newer. I chose the latter.
Hey Eggman–
That’s great info re: the 8-character password limitation. I’ve run into that as well. Thanks for sharing that.
–DW
So did anyone get 6248 and/or 8024 working with a windows 2008R2 NPS implementation?
Howard–
Yes! This post was updated in August with what you needed to accomplish. Scroll up to the few paragraphs above the comments. This was resolved with a proper understanding of the $enab15$ username.
–DW
Has anyone tried 54xx, NPS with Port Authentication? We’re having some odd issues. With clients not being able to reconnect
Been banging my head against this for HOURS and just did the $enab15$ username trick. Thanks for the tip.
Following this guide wasn’t the end for me. I also had to add a “Connection Request Policy” which pretty much mimicked the settings that you provided in this guide. Once I added a policy under connection request policies, all of our domain admins were able to authenticate. Thank you so much for getting us headed in the right direction. I was lost without it!
So did anyone get 5448 working with a windows 2008R2 NPS implementation
Thanks for the great post.
FYI, I ran into an issue with my PowerConnect 6224, 3.3.13.1, VxWorks 6.5. The radius key length could only be 48 characters or shorter to a 2008R2 NPS. The radius server would accept the incoming request but kept saying the user failed authentication.
And make sure to reload the switch after initial radius setup. Everything started working better after a reload.
Nice article. Thumbs up 🙂
I` trying to configure DELL switches and everywhere is describe to use unsecure PAP for communication.
Is it possible to force secure communication and use ms-chap-v2 beetwen Dell powerConnect and radius server 2012R2?