tunnel-group PUBLIC.IP.OF.IPCOP type ipsec-l2l
tunnel-group PUBLIC.IP.OF.IPCOP general-attributes
default-group-policy IPCopVPN
tunnel-group PUBLIC.IP.OF.IPCOP ipsec-attributes
pre-shared-key strongpassword
Obviously, you need to change "strongpassword" to be a strong shared password that you will authenticate your remote IPCop box to this Cisco ASA to create the tunnel.
Great, now the Cisco ASA 5520 configuration is complete. Off to IPCop.
IPCop – Running version 1.4.16 – STO Campus Connection – Configuration Details
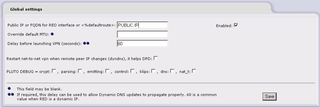
Launch the IPCop Interface, http://IPCOP.IP:81, and click on VPNs -> VPNs menu like below
When the VPNs menu launches, you'll need to verify a few things… Make sure you settings look like below… have your PUBLIC IP in the appropriate box, click the Enabled checkbox, and click Save.
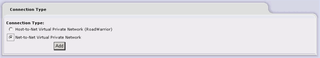
Great, now you need to create a tunnel. Click the Add button. Now, choose "net to net" and click Add.
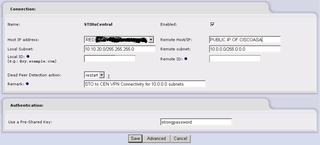
Make your settings like below… Pay particular attention to the order of the subnets. In this example, the Host IP Address is the PUBLIC.IP of the IPCop box – the RED Interface. The rest of it should make sense – working backwards from the Cisco ASA Config. The Local subnet is the subnet behind the IPCop box (ala: the Remote_Network on the Cisco ASA) and the Remote HOST is the PUBLIC.IP of the Cisco ASA and the Remote Subnet is any subnet(s) that are at the Central location behind the Cisco ASA. Make sense?
Anyway, click Save. You're network will now show up like below.
Check that out… it's RED and Closed. That's normal. Click the little arrow next to the RED Closed status. Your screen will refresh, and, assuming you configured everything properly, your VPN tunnel will connect.
Hooray! Your VPN tunnel is now GREEN and Open.
I'm blogging this because it's been on my mind lately. Why you say? Because we still use this connection at our STO Campus. And, randomly, we will lose connection. We have a dynamic IP – because BTC won't give us static IPs. So, from time to time, we need to rebuild this connection because the PUBLIC.IP on the IPCop box will change. It's very annoying. It's happened several times recently – including yesterday – so it's fresh on my mind and I wanted to capture the info somewhere in hopes that it helps someone else. G'nite!



Hi,
very nice work.
I’m trying to get data packets over my “asa 5505 (8.4(1)) to ipcop 1.4.21 ipsec”-connection.
The tunnel is green, but pings and other data is not going thru the tunnel. The ipcop has BOT on it, and I set it to “permit any to any” so that there are no packets to be dropped/rejected (also on the asa).
Do you have an idea? How did you set routing/exempt rules or nat on the asa?
best regards
Erik
Erik–
When I’ve seen this in the past, it’s been many years, but when I’ve seen it – it’s related to ACL “reflection”
Whatever you identify as interesting/ACL traffic on one side, needs to be reflected/mirrored on the other.